CTBUCTF 2024 个人赛-ranfey-wp
简单总结
前两天队名是少终的小千,后面改为了fufu吃大米
总排名第二
解题情况
| # | 题目名称 | 类型 | 情况 |
|---|---|---|---|
| 1 | 二向箔 | Misc | 一血 |
| 2 | 网络迷踪✈ | Misc | 解出 |
| 3 | 签到 | Misc | 解出 |
| 4 | EZ_Caesar | Crypto | 解出 |
| 5 | EZ_MATH | Crypto | 一血 |
| 6 | 最后的晚餐 | Crypto | 一血 |
| 7 | ez_RSA | Crypto | 解出 |
| 8 | Chaining | Crypto | 二血 |
| 9 | b了b了别打了 | Web | 三血 |
| 10 | EZ_login | Web | 一血 |
| 11 | 重生之我不是大宝 | Web | 解出 |
| 12 | random | Reverse | 解出 |
| 13 | easy_z3 | Reverse | 一血 |
| 14 | 简单的逻辑 | Reverse | 一血 |
| 15 | sign_in | Reverse | 一血 |
拿了7个一血,第一次这么多
非常爽刷
其实处处碰壁(
还是有很多遗憾,很多题就是差一点,看[G3rling](G3rling's Blog – 江泠间)师傅的wp自己要被自己气死qwq
也挂一下其他师傅的wp链接
CTBUCTF 2024 Writeup – G3rling's Blog
CTBUCTF 2024-Lwrzgo's blog!!!!!
Misc
二向箔
下载下来得到这些文件
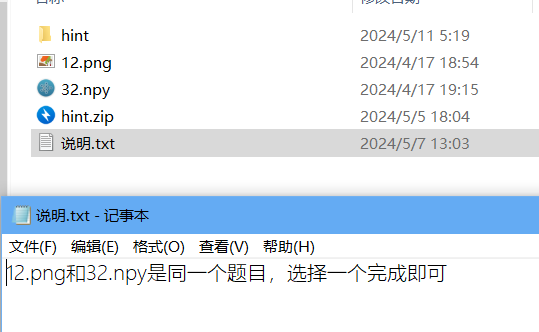
hint里面是xml,后面说是可以改后缀变为word不过我没看
以及,正确解法应该是去用库,等待官方wp
12.png是一个1*262144的图像,先010看文件,结构都没什么问题,看到文件尾在正常结束后又跟了一串
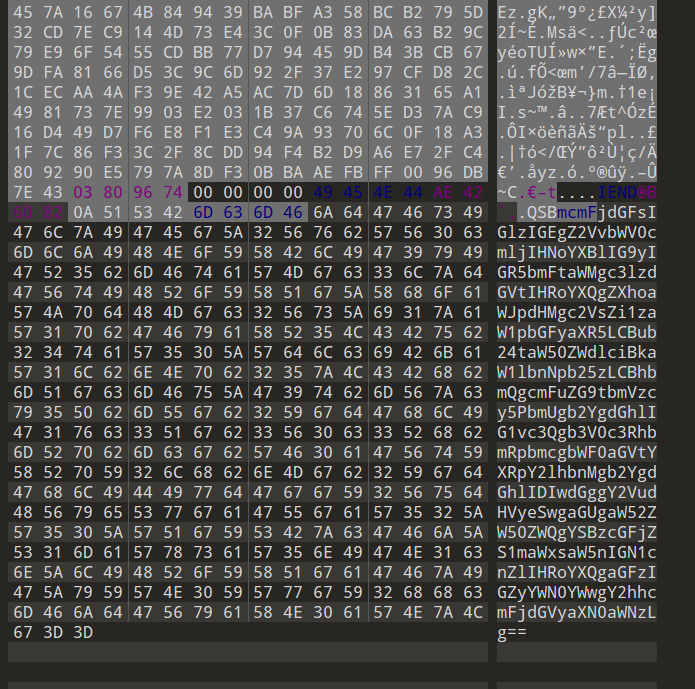
BASE64一眼顶真
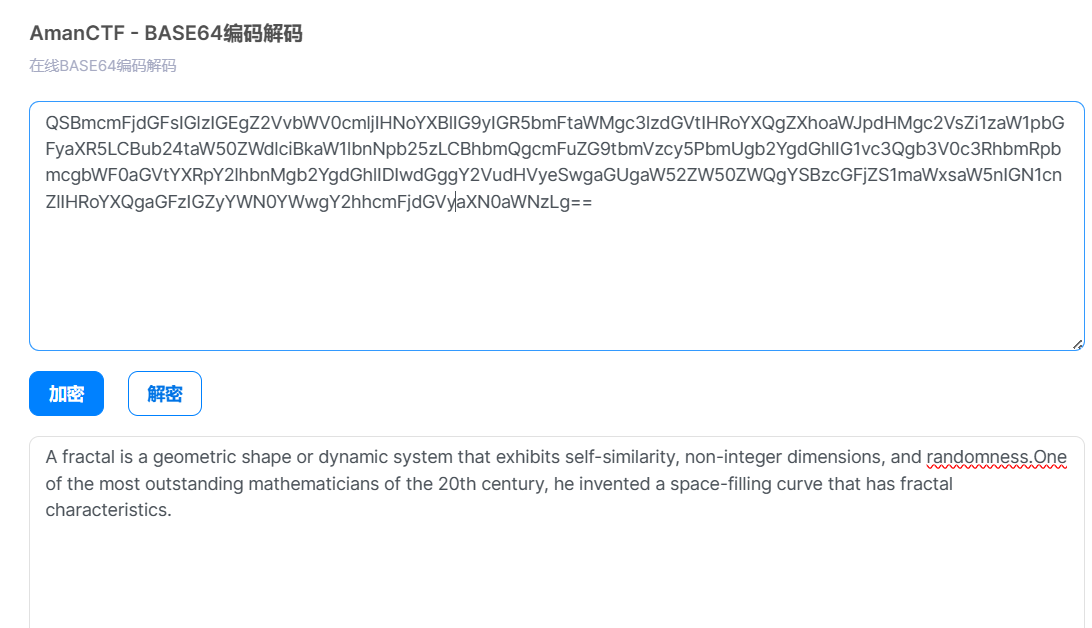
然后翻译过来是
去搜索之后得到可能是皮亚诺曲线或者希尔伯特曲线
让gpt写了皮亚诺曲线结果感觉不对然后又写了希尔伯特曲线的就跑出来了
import numpy as np
from PIL import Image
def xy_from_d(d, n):
x, y = 0, 0
t = d
s = 1
while s < n:
rx = 1 & (t // 2)
ry = 1 & (t ^ rx)
x, y = rotate_and_flip(s, x, y, rx, ry)
x += s * rx
y += s * ry
t //= 4
s *= 2
return x, y
def rotate_and_flip(n, x, y, rx, ry):
if ry == 0:
if rx == 1:
x = n - 1 - x
y = n - 1 - y
return y, x
return x, y
def hilbert_curve_transform(one_d_array, n):
if len(one_d_array) != n * n:
raise ValueError("The length of the array must be n^2.")
two_d_array = np.zeros((n, n))
for i in range(len(one_d_array)):
x, y = xy_from_d(i, n)
two_d_array[x, y] = one_d_array[i]
return two_d_array
input_path = "12.png" # 一维图像文件的路径
output_path = "22hilbert_image.png" # 保存转换后的二维图像文件的路径
# 加载图像并转换为灰度
image = Image.open(input_path).convert("L")
one_d_array = np.array(image).flatten()
# 检查一维数组长度是否为262144
if len(one_d_array) != 262144:
raise ValueError(
"The input image size must be exactly 512x512 pixels when flattened."
)
# 转换到二维
n = 512 # 选择一个合适的n值
two_d_array = hilbert_curve_transform(one_d_array, n)
# 将结果保存为图像
two_d_image = Image.fromarray(two_d_array.astype(np.uint8)) # 确保数据类型正确
two_d_image.save(output_path)
然后一个个拼起来得到

coctf{d3str0y1ng_y0u_h4s_n0th1ng_t0_d0_w1th_y0u}
网络迷踪✈
唉,ctf秀恩爱
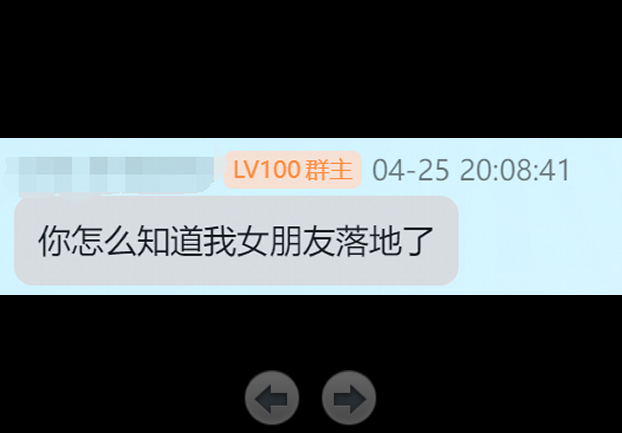
根据时间和地点,川外是在重庆,用软件搜索
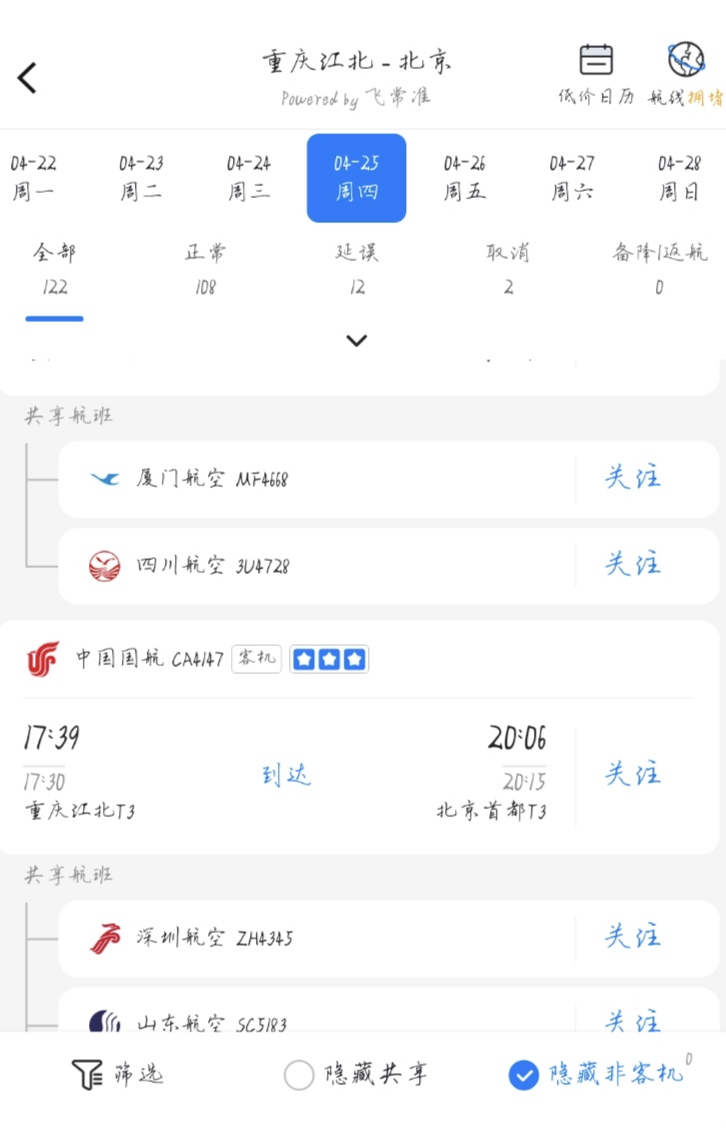
我把成都的全试完了才想起来川外是在重庆(明明这就是我日语n2考点),服了
coctf{CA4147}
签到
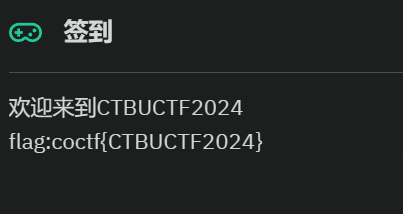
coctf{CTBUCTF2024}
Crypto
EZ_Caesar
题目为
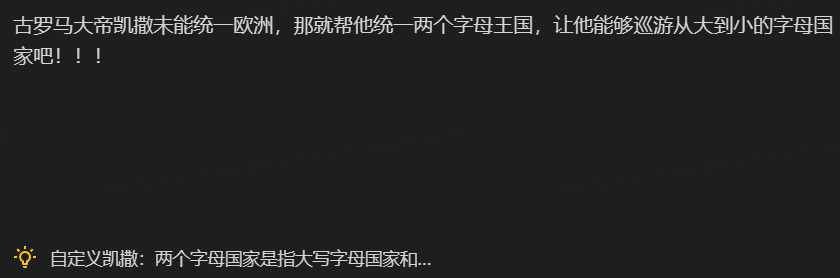
kwkBn{LOJfRFAumEqzFMvdKlMfsEPbEXGQtImjGZZM}
先使用凯撒枚举
不过是错的
hint出了才明白怎么回事,大写到小写
是按照ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz的偏移
自己对了一下,向右偏移44个

gpt写了个小脚本
def substitution_cipher(text, key):
alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz"
substituted_alphabet = key + key.upper()
substituted_alphabet = substituted_alphabet[:52]
table = str.maketrans(alphabet, substituted_alphabet)
return text.translate(table)
# 提供的两个字母表
original_alphabet = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz"
substitution_alphabet = "stuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqr"
text = "kwkBnLOJfRFAumEqzFMvdKlMfsEPbEXGQtImjGZZM"
encrypted_text = substitution_cipher(text, substitution_alphabet)
print("加密后的文本:", encrypted_text)
coctf{DGBXJxsmewirxEnVCdEXkwHTwPyIlAebyRRE}
EZ_MATH
题目为
import uuid
import libnum
from Crypto.Util.number import getPrime
flag = "coctf{" + str(uuid.uuid4()) + "}"
m = libnum.s2n(flag)
p = getPrime(512)
q = getPrime(512)
n = p*q
e = 0x10001
c = pow(m, e, n)
hint = p**6 - q**3
print(f"n = {n}")
print(f"e = {e}")
print(f"c = {c}")
print(f"h = {hint}")
#n=116647486482136197425951596620969966886506891446362122370218350716511525865224484873789787581652498238455119680987889232828091923454203497998697115445887420129933827437297306944736650019282521852328419318560735286602226819612740015575186864400257763600635308240990166046247050412450770882691954269489106373129
#e=65537
#c = 96767072250276945659137295570949648070358997224893963422504633350407081588891760900513449728716563526777201052161290301199279394139527500340587316767208664845655282036731580669507375766580456789009309705592838157405099333332191316809633866736076801898777418304924846229755247474929419003003575295067033863845
#h = 464359967935511579153548436604011415649032210108926934628244059661300636954750206045965156233958290665125008281945496822913269100110298831914446931894316416832431068416425690499675233533084875328874289374277042756451334781649509280116998915853080121579985497172717274230266936857416954879651774308685726581526678142913307494837050411230435029502546350358673339698736346953002124967577503542780826649645880219786166936245546255132927143523318960418906889813832538557541964483613264496813440423101390388786747184363947466535545808042562831962362194112931658004559727575444604487042782376838361658857700823527363305898996145191641714779492635146423786413703141170778538329513308542467221169228104456350700128852674871024907359205508782112657289264674996399601109793172971107743954660753682565988236343231345008055243304748676592441846922055765312098923200408114980057070444992755391317796301815295468747424323284338552104605486看起来很多,其实就是普通的解方程起手
n = p*q
hint = p**6 - q**3
解得
p = 8799860659697425371171754992340275739828805826699472115992599051593443246763540975911428834651636001810317644682004229683894331897205603487851483714301747
q = 13255606082079373233635973277399218110165273490679442032052911688410304542507612195223014489043236837553581498186138035640581860885798916135781441958154707然后接着用现成脚本
def extended_gcd(a, b):
if b == 0:
return a, 1, 0
else:
d, x, y = extended_gcd(b, a % b)
return d, y, x - (a // b) * y
def mod_inverse(a, m):
d, x, y = extended_gcd(a, m)
if d != 1:
raise ValueError("")
else:
return x % m
def ttt(c, e, n, p, q):
# 计算 phi(n)
phi_n = (p - 1) * (q - 1)
# 计算 d,满足 d * e ≡ 1 (mod phi(n))
d = mod_inverse(e, phi_n)
# 计算 m
m = pow(c, d, n)
return m
e = ttt(c, e, n, p, q)
flag = libnum.n2s(e)
print("flag =", flag)得到
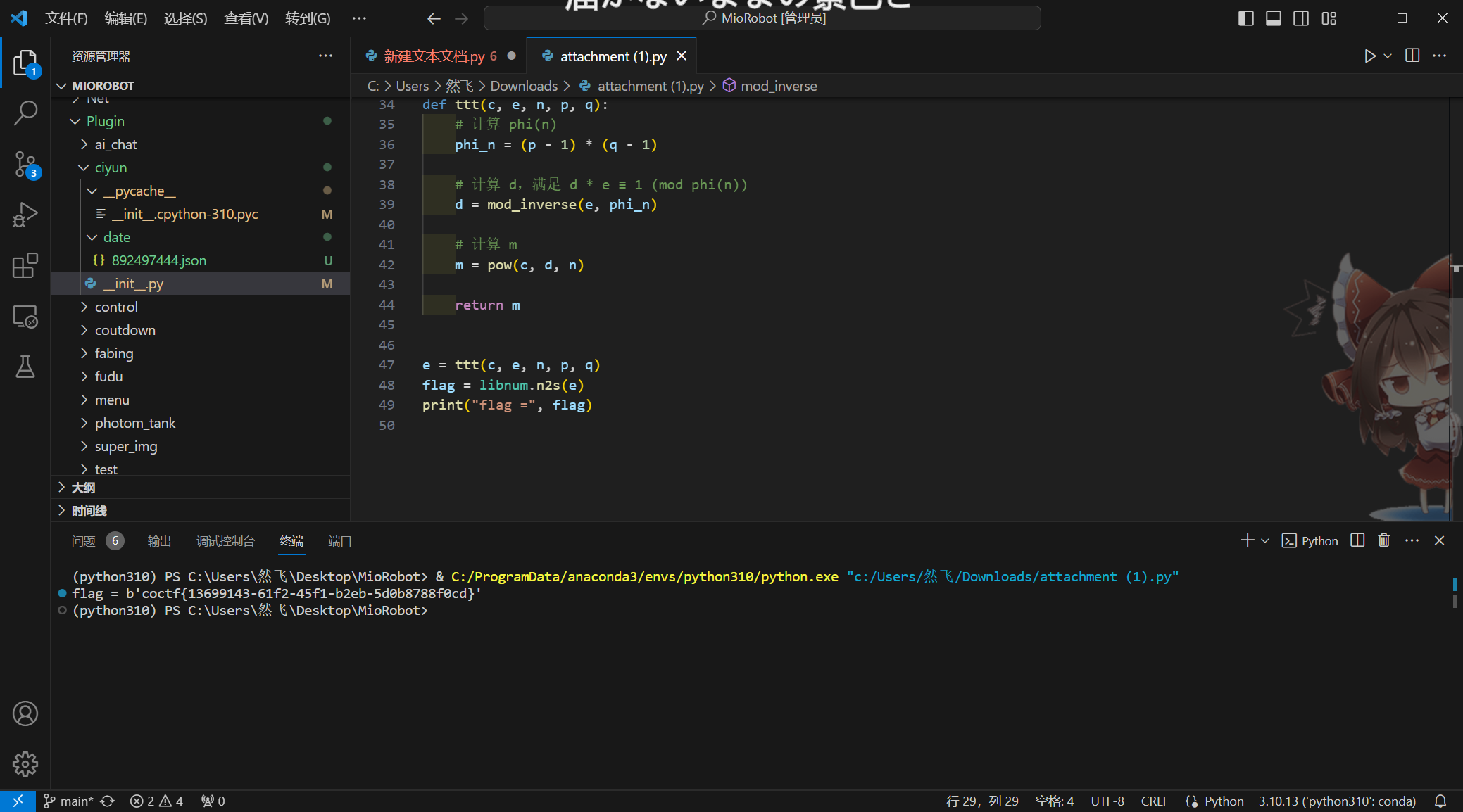
coctf{13699143-61f2-45f1-b2eb-5d0b8788f0cd}
最后的晚餐
题目为
import random
import uuid
import libnum
import gmpy2
flag = "coctf{" + str(uuid.uuid4()) + "}"
m = libnum.s2n(flag)
e = random.randint(1,20)
n_values = []
c_values = []
for i in range(8):
while True:
p = libnum.generate_prime(504)
q = libnum.generate_prime(504)
n = p * q
phi_n = (p - 1) * (q - 1)
if gmpy2.gcd(e, phi_n) == 1 and phi_n % e != 0:
break
current_n = n
current_c = pow(m, e, n)
n_values.append(current_n)
c_values.append(current_c)
print("n=", n_values)
print("c=", c_values)
#n=[1202696364148455389632161263939746733867966583846761504559461939745614028803878758527893159335157812165555143285753969552515473799821561952128746378098873154747434777765527800129244815051303696415318022485463986480873077329092243399286834394501520243539681825137538558309234940336375160693478810321362591, 1303220834677808190382592586462226978162436770681912619134208151631521296406728705825945758440943249600669090980931293537378580725508048464762478103214525663634254673878669845248890392692369729166044498219095139875262656152039369545479710252797788380561124568789756419544507988953951384483255087323798301, 1362675074871299335744848842449269167351305397862620168517903968837511870754904146535103948270433790436960049765138994980939038574570789216498486890065560280449014303282448806935122637706295635365214457586473359758066899955606084371809929567414504097607716245751874505778715689541996527680535326669692243, 1775683723488140552419653540034216829007271626503380430509397027574177014578046535589503643234339808578581852571454086391622793528555249535188374856589068393174403034316567450208830720789296800132802013663793449348635055791342684401482713965897761826222553840754337875112897239349704752141635189387176373, 1511457727293815588021174067186969658072093754178359998104367590903674384784671525703179034351339190699906265620657449545018681299013900772903757400248972797738341308534891975376914078357877847064661367673813329205757710761553935181869982216545789919300363602357449115589671238753338752172656139152392871, 1340284916102131743873092646428301040718254113309227872940244217393080180336698750290480002109455045782628077766922228671793725606626887343366284036645916695542161346336648421409932396071695072842771775545214041381647258806600401104806145915198481821227365587285897904536289893972784481332987364820544807, 1412018378503982837678891568247623687969755347356687447901612245922053609445483518835647268486824247689598694500668327376870041406636441267383753429404360003664504236603212725474654772392598722377298816502517480208074782012357698046970236009106716002242931060954733954557484459351324647241372084370237081, 960179367485450649874723114784061067430337710631858604558161076915682362606249974275865395738304006847406852400592551088645156973746360355669760195754858746043397228006407846505613288605092128481553218245824254530388334732238111594847253952320109631075191089610282795217690221093314886174181502973241949]
#c=[1183820152440430028728799872500022322491370240583649092428217830995787239188901048704944150598360827123765723051353793985556700355204805054762672817660172876880931583120253653031474979842728984352699340186107042926552338619216525929973427052202426498220093290827605602687503822106373993041799498634942264, 46524109952894248945723126525535093905100342743888990231003636501832273970066918421312505952077837281121848798744364827737007818409543192099397110007081611756945560191862029285278190799985198334966292519832989747145062299695508217999316111887749515287770843574817174103728087761426808848038000805252574, 1099008260985402626216609670314286436568679979317578484513216598511289613109096855675926860686696044167513955410614551223132874956570657025296369403166964989803486447583576755723649529413827094820552533451297077226220981013438816822641594597020244890309236666470642813968530385064768572787366860692559122, 405988054707690581694531311307268953385872627403271255474751396720500497452348019920978385637092940310780471476277362749613004161351555088963829477523971620020740458301702614525746936180547688393607365022866366502219010082560107545548144755116602330676042737786701657104695173120758912083722516372211051, 1328380972413147833520100546314727665661714571112051869435209232898735372951454846555988801345711732157707626096552189936150026961086124045236145796831802367574802846302409653952949869179357644154362786313487304774882679783772547477203061746919130416249534932190991664581091421963081891994548337208073773, 175342439627948719835032555011918574826210288781456677273356388588022810196987669603462633599477611063847518301124041606146271263573640615245495533694753093900916987748042006991185841214437163701416160239823833168009829241380184158464898799730685306394042763032017217585301756171234868808384533483358815, 1316419045857130520163128929921428277126487633849519328127144181009173866003926462860012484388329499805010562635526638255732538005893356011803054759727708783575871912775540734321452088360953029759708959373601779334764873669129085432874416596858633147347489128158492182846764544409499954996618096210087180, 561522181579558819748607385151514502117755147326363022827669703787478829609191142865353069106923683816812366971271878380383704784759866352622167004527323856039569243367314224641625955008131517980673703855659688062747656939148510052724222576349218672295666354233713799518076708495550790550945310797373473]这么多n和c,先考虑用共模攻击脚本
import gmpy2
from sympy.ntheory.modular import solve_congruence
import libnum
n = []
c = []
def common_modulus_attack(e, ns, cs):
# 使用中国剩余定理解决同余方程
congruences = [(c, n) for c, n in zip(cs, ns)]
m_crt, _ = solve_congruence(*congruences)
m = gmpy2.iroot(m_crt, e)[0]
return m
for length in range(1, 20):
m_recovered = common_modulus_attack(length, n, c)
flag = libnum.n2s(int(m_recovered))
print("Flag:", flag)
if "coctf" in str(flag):
break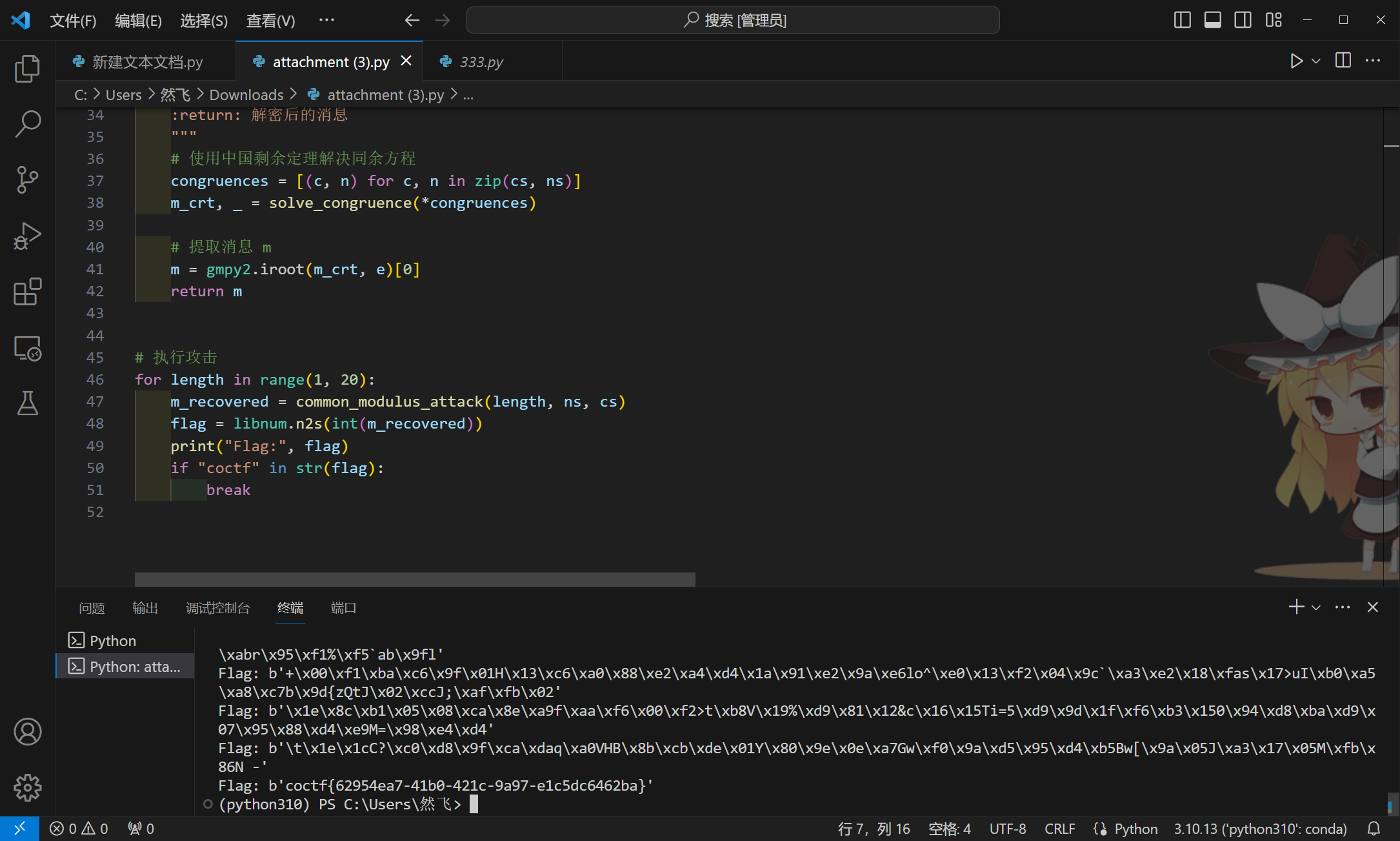
coctf{62954ea7-41b0-421c-9a97-e1c5dc6462ba}
Chaining
刚拿到的时候为一个无法打开的文件,用Notepad打开
把null删除
题目为
import uuid
from Crypto.Util.number import *
import random
flag = "coctf{" + str(uuid.uuid4()) + "}"
flag_bytes = flag.encode('ascii')
IV = bytes_to_long(b'cbc!')
K = random.randrange(1,1<<30)
block_length = 4
flag_bytes = flag_bytes + ((block_length - len(flag_bytes) % block_length) % block_length) * b''
plain_block = [flag_bytes[block_length * i: block_length * (i + 1)] for i in range(len(flag_bytes) // block_length)]
c = []
c0 = (IV ^ bytes_to_long(plain_block[0])) ^ K
c.append(c0)
for i in range(len(plain_block)-1):
c.append(c[i] ^ bytes_to_long(plain_block[i+1]) ^ K)
print(f"#c={c}")
#c=[444435836, 1719035238, 1228115246, 1646734693, 1097110369, 1864640302, 1483579198, 1898981934, 1596375909, 644053546, 1562479107]一个个规则分块,可以知道是CBC模式的加密
block_length = 4
*flag_bytes = flag_bytes + ((block_length - len(flag_bytes) % block_length) % block_length) b''**
由此判断分块为4个字符,就是coct
from Crypto.Util.number import bytes_to_long
# 已知或猜测的数据
IV = bytes_to_long(b"cbc!")
c0 = 444435836 # 这是已知的第一个密文块
# 明文块的假设
plain_block_0 = b"coct"
plain_block_0_long = bytes_to_long(plain_block_0)
# 计算 K
K = (IV ^ plain_block_0_long) ^ c0
print(f"Calculated K: {K}")得到k为443583785
然后根据cbc脚本,链式解密
from Crypto.Util.number import bytes_to_long, long_to_bytes
IV = bytes_to_long(b"cbc!")
c = [444435836, 1719035238, 1228115246, 1646734693, 1097110369, 1864640302, 1483579198, 1898981934, 1596375909, 644053546, 1562479107]
K = 443583785
# 初始化明文块列表
plaintext_blocks = []
# 解密第一个明文块
first_plain_long = (IV ^ K) ^ c[0]
plaintext_blocks.append(long_to_bytes(first_plain_long))
# 解密后续明文块
for i in range(1, len(c)):
plain_long = (c[i - 1] ^ K) ^ c[i]
plaintext_blocks.append(long_to_bytes(plain_long))
# 显示解密后的明文块
decrypted_message = b"".join(plaintext_blocks).decode("ascii")
print("Decrypted message:", decrypted_message)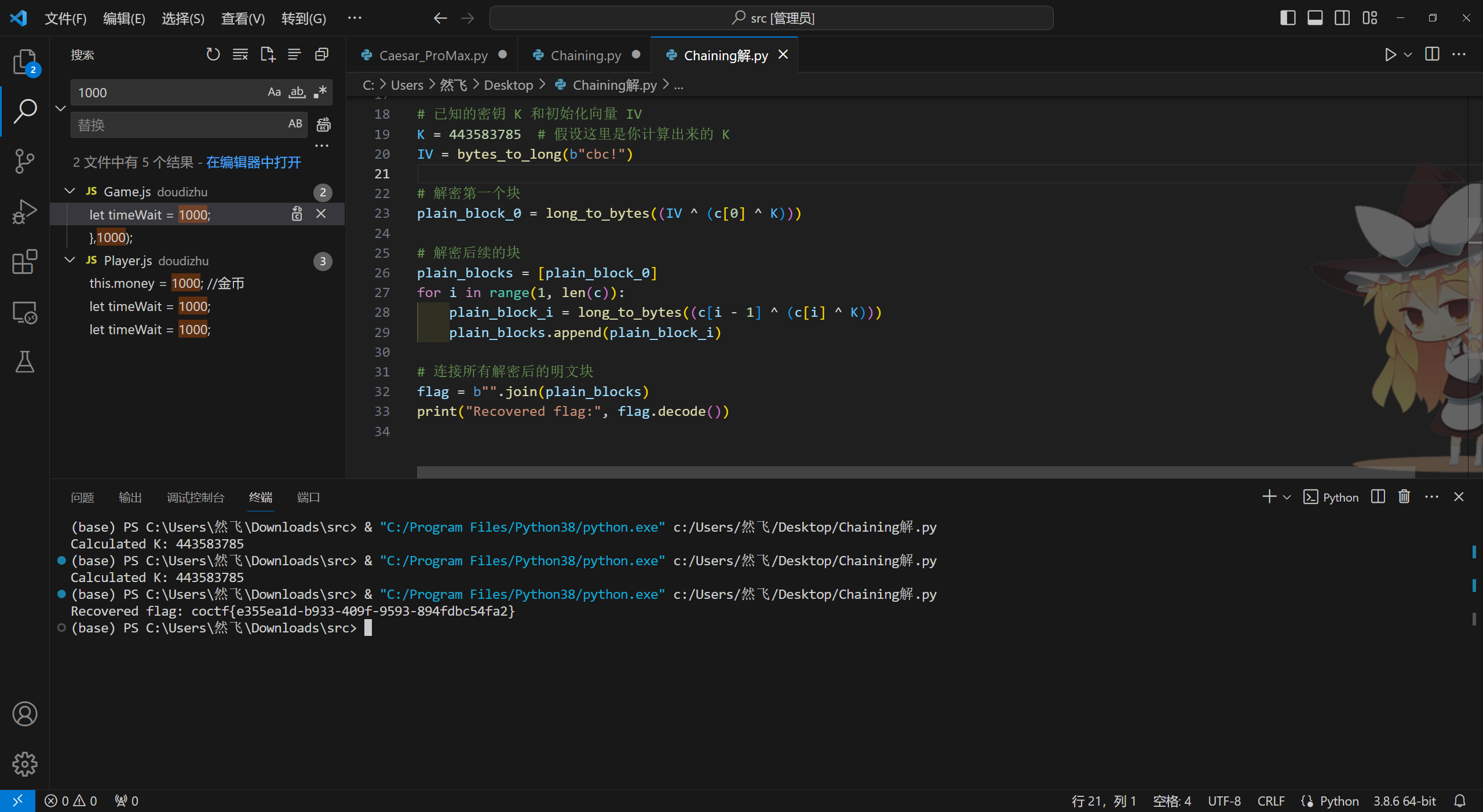
coctf{e355ea1d-b933-409f-9593-894fdbc54fa2}
ez_RSA
题目为
import libnum
import uuid
import random
flag = "coctf{" + str(uuid.uuid4()) + "}"
m = libnum.s2n(flag)
p = libnum.generate_prime(512)
q = libnum.generate_prime(512)
n = p * q
phi_n = (p-1)*(q-1)
while True:
nbits = 1024
d = random.getrandbits(nbits // 4)
if (libnum.gcd(d, phi_n) == 1 and 36 * pow(d, 4) < n):
break
e = libnum.invmod(d, phi_n)
c = pow(m, e, n)
print("n=",n)
print("e=",e)
print("c=",c)
#n=97402143456873630947919560513889485505969250585496924927194725330659766711511705362087553992914530797867348204963538411612462773296789731668721614131637002811159584334122418227667903938264681606161103564136196384702124149241068764859485060650091606049822529566575423061235752004172350079255494867330383857373
#e=60162413832198280128952061095938226933468842632504652476614784098872635050461918473880877908324948476540594350306656598992779690526586645623310259558677422424807540709392763219230493089930870894324783222757861104891892161699077441187584019958927752461071152873194288661279831201917336761994145759399707977029
#c=24742955067375668648075105357354845040871706853601984082437987460176053419945825023321937186638028034238507829935601334983577459486608336100712381376562229575705380447653007705888455162966843843853534336551483249785926951218116546085417926434932767587674068103696243415541019495766931144362070166324340915347d 是通过 nbits // 4 生成的, nbits 是 1024,d 相对于 n 足够小,用Wiener攻击
import math
import libnum
def continued_fraction(numerator, denominator):
while denominator:
whole_part = numerator // denominator
yield whole_part
numerator, denominator = denominator, numerator - whole_part * denominator
def convergents(continued_fraction):
convs = []
for i in continued_fraction:
if not convs:
convs.append((i, 1))
elif len(convs) == 1:
convs.append((i * convs[0][0] + 1, i))
else:
h = i * convs[-1][0] + convs[-2][0]
k = i * convs[-1][1] + convs[-2][1]
convs.append((h, k))
yield convs[-1]
def wiener_attack(n, e):
for k, d in convergents(continued_fraction(e, n)):
# 检查当前的 k/d 是否是有效的私钥
if k == 0:
continue
phi_n = (e * d - 1) // k
# 通过解方程得到可能的 p 和 q
a = 1
b = -(n - phi_n + 1)
c = n
discriminant = b * b - 4 * a * c
if discriminant >= 0:
root_disc = math.isqrt(discriminant)
if root_disc * root_disc == discriminant:
p = (-b + root_disc) // (2 * a)
q = (-b - root_disc) // (2 * a)
if p * q == n:
return d
return None
n = 97402143456873630947919560513889485505969250585496924927194725330659766711511705362087553992914530797867348204963538411612462773296789731668721614131637002811159584334122418227667903938264681606161103564136196384702124149241068764859485060650091606049822529566575423061235752004172350079255494867330383857373
e = 60162413832198280128952061095938226933468842632504652476614784098872635050461918473880877908324948476540594350306656598992779690526586645623310259558677422424807540709392763219230493089930870894324783222757861104891892161699077441187584019958927752461071152873194288661279831201917336761994145759399707977029
c = 24742955067375668648075105357354845040871706853601984082437987460176053419945825023321937186638028034238507829935601334983577459486608336100712381376562229575705380447653007705888455162966843843853534336551483249785926951218116546085417926434932767587674068103696243415541019495766931144362070166324340915347
d_found = wiener_attack(n, e)
if d_found:
print("Found d:", d_found)
# 解密信息
m = pow(c, d_found, n)
print("Decrypted message:", libnum.n2s(m))
else:
print("Failed to find d using Wiener's attack")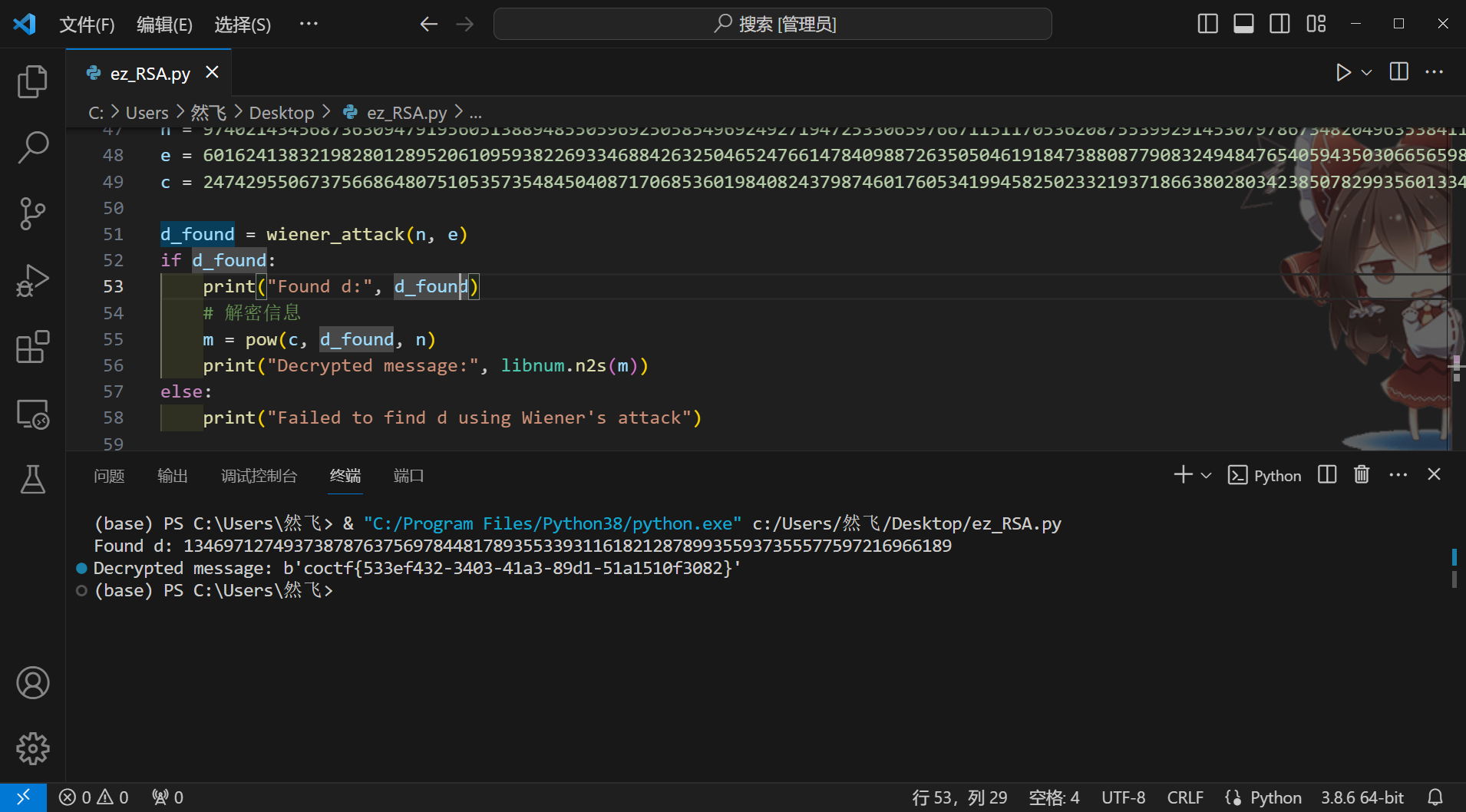
coctf{533ef432-3403-41a3-89d1-51a1510f3082}
Web
b了b了别打了
看题目有给出建站文件,直接看关键文件
const {VM, VMScript} = require('vm2');
const flag = process.env.FLAG || "flag{test}";
const notes = [
"加油,你是最棒的!",
"每一次尝试,都是一次成长。",
"不要害怕失败,它是成功的垫脚石。",
"坚持就是胜利。",
"只有你相信自己,别人才会相信你。",
"你可以的,别放弃!",
"星空也会照亮你前行的路。",
"你只有一次生命的机会,所以要做自己想做的,去追求自己想追求的。",
"你已经走了这么远,别放弃!",
"抬头看看星空",
"星空不问赶路人,但会陪伴每一个努力前行的你。",
"加油吧!不止是因为这道题,还有你的未来。",
];
let err = "flag{test}";
var data = "";
function check(data){
data = data.inputValue
err = notes[Math.floor(Math.random() * notes.length)];
code = `
var o = (function() {
var obj = {
a: 1,
flag: "${flag}",
};
return {
get: function(k) {
return obj[k];
},
add: function() {
n++;
}
};
}
)();
try {
`+
data
+
`
function checkFlag() {
if (o.get("flag") !== "${flag}") {
return "${flag}";
} else {
return "${err}";
}
}
checkFlag();
} catch (e) {
a = "${err}";
}
`;
const script = new VMScript(code);
const result = new VM().run(script);
console.log(result);
return result;
}
module.exports.check = check;
可以看出来是在沙箱里面{VM, VMScript} = require('vm2');
传入的值key为inputValue会在被传入/package1.js处理,最后读取到上图的data进行拼接
因为下面是用o.get的方法获得flag的,然后又有一个判断,让其不相等就会得到flag的返回
那就直接修改o.get = function(k) { return 4 }随便返回点东西(不过要数字)
得到
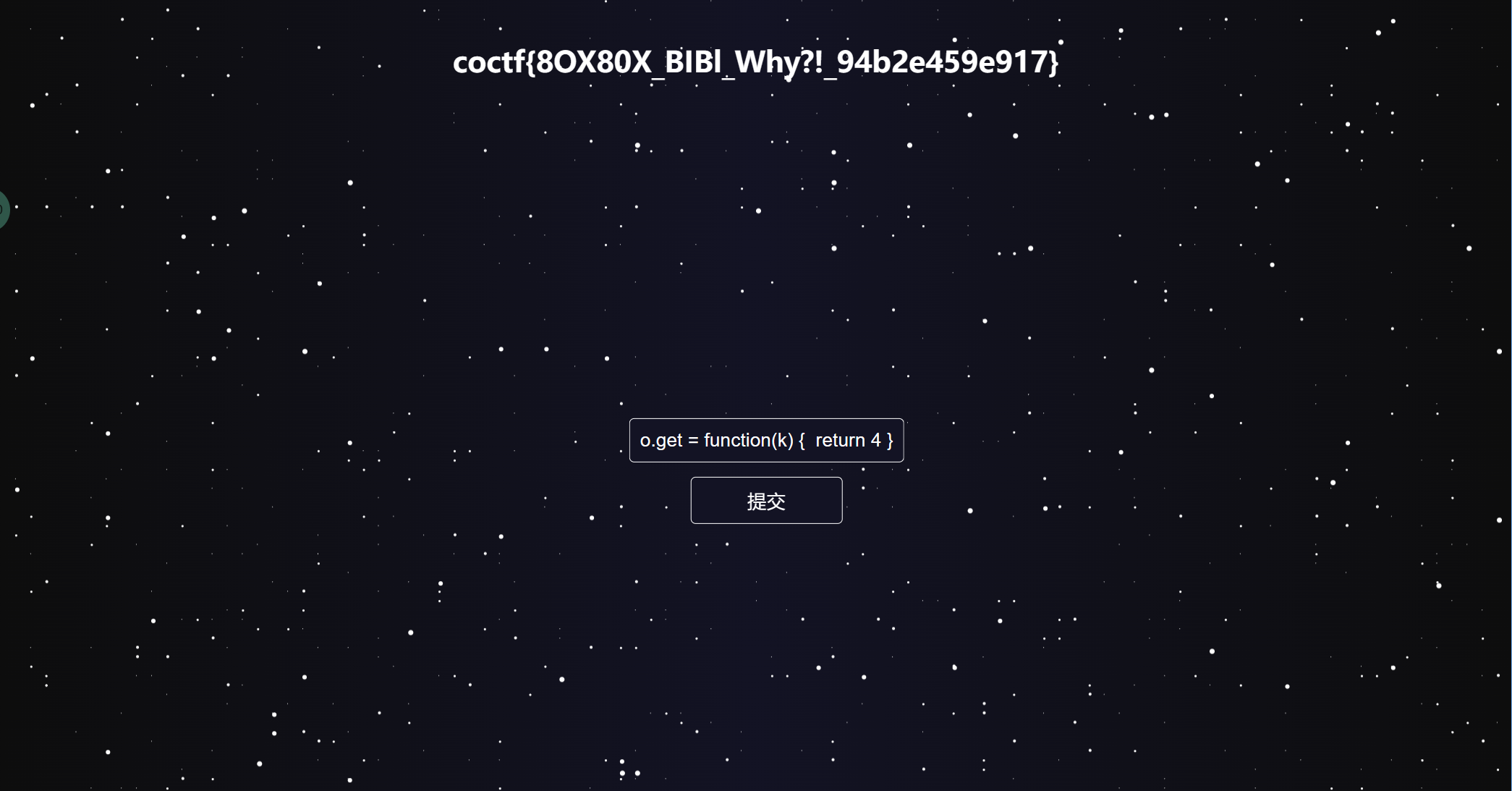
coctf{8OX80X_BIBl_Why?!_94b2e459e917}
EZ_login
题目没给文件
先F12,然后直接看到邮箱admin@ooxuan.com
刚开始不会做,只是感觉忘记密码那有东西但是不会搞(还一直拿字典爆破)
后面有提示host poisoning(host头攻击)
去搜了知道了(学到了)
因为服务器和我们环境都是在校园内网,先开nc监听端口,然后我有路由器还要端口映射(记得关防火墙开放端口)
还要先知道自己的校园网ip
之后进入忘记密码界面,抓包
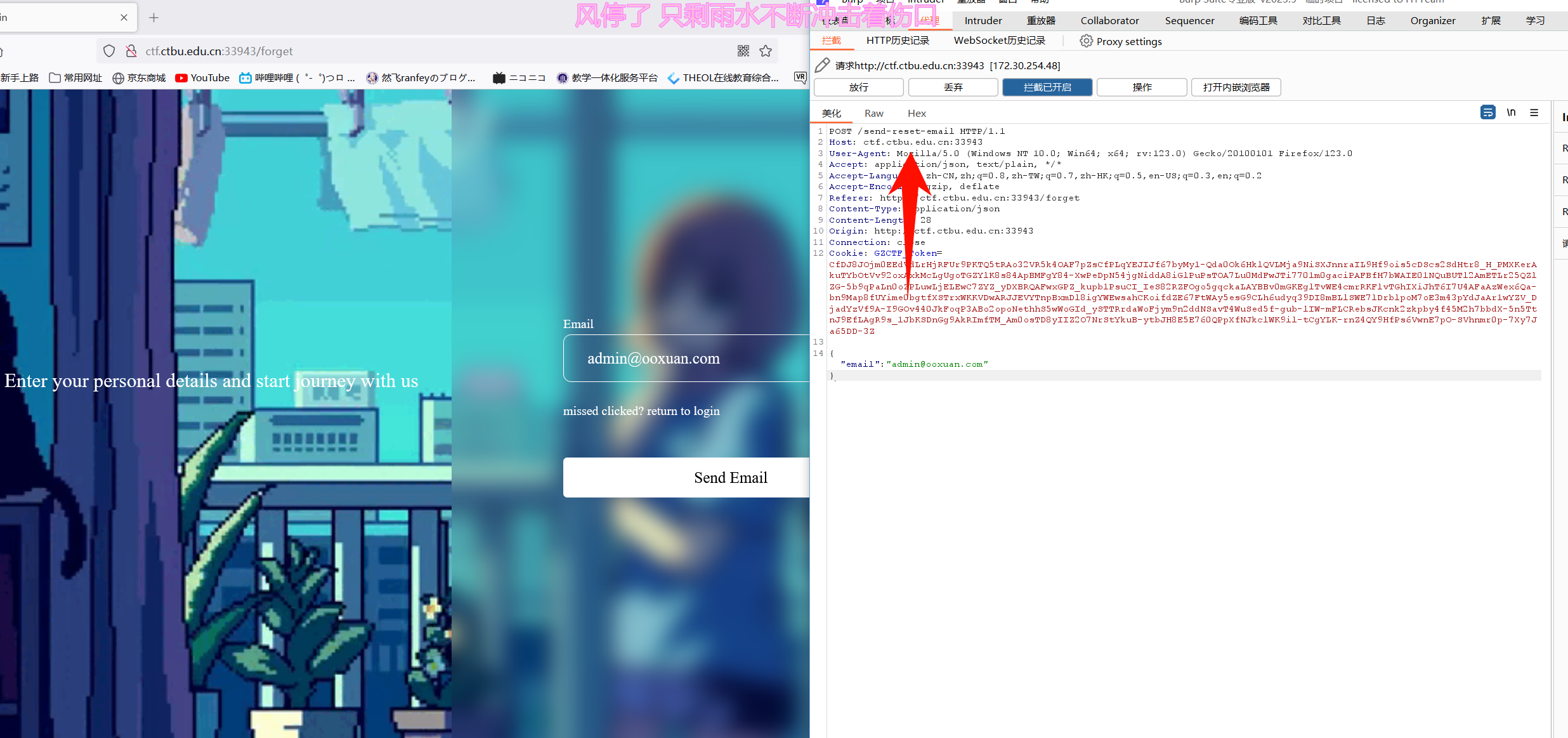
修改host头为自己的ip加监听端口
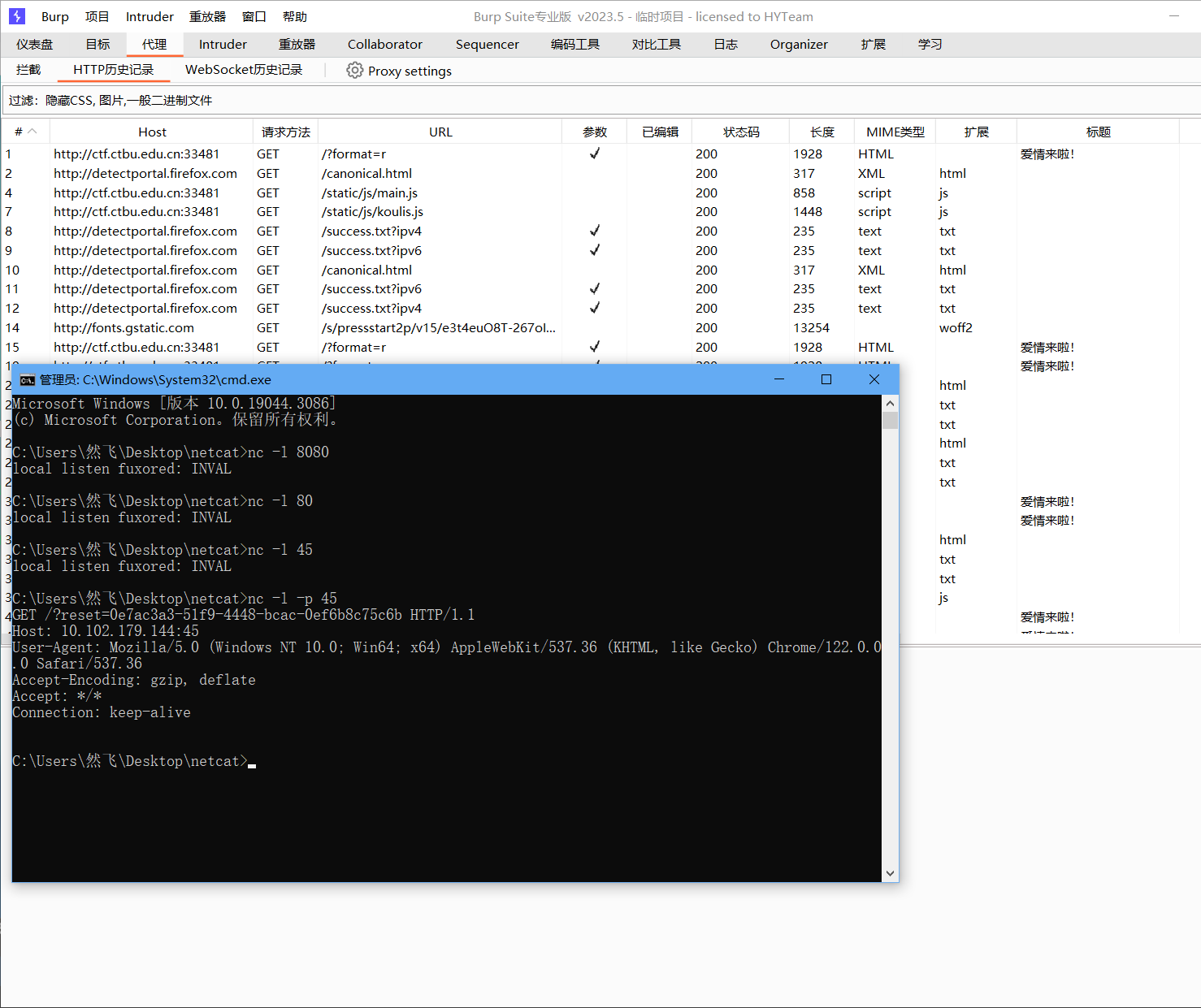
得到请求的地址,直接加到后面访问进入了修改密码界面
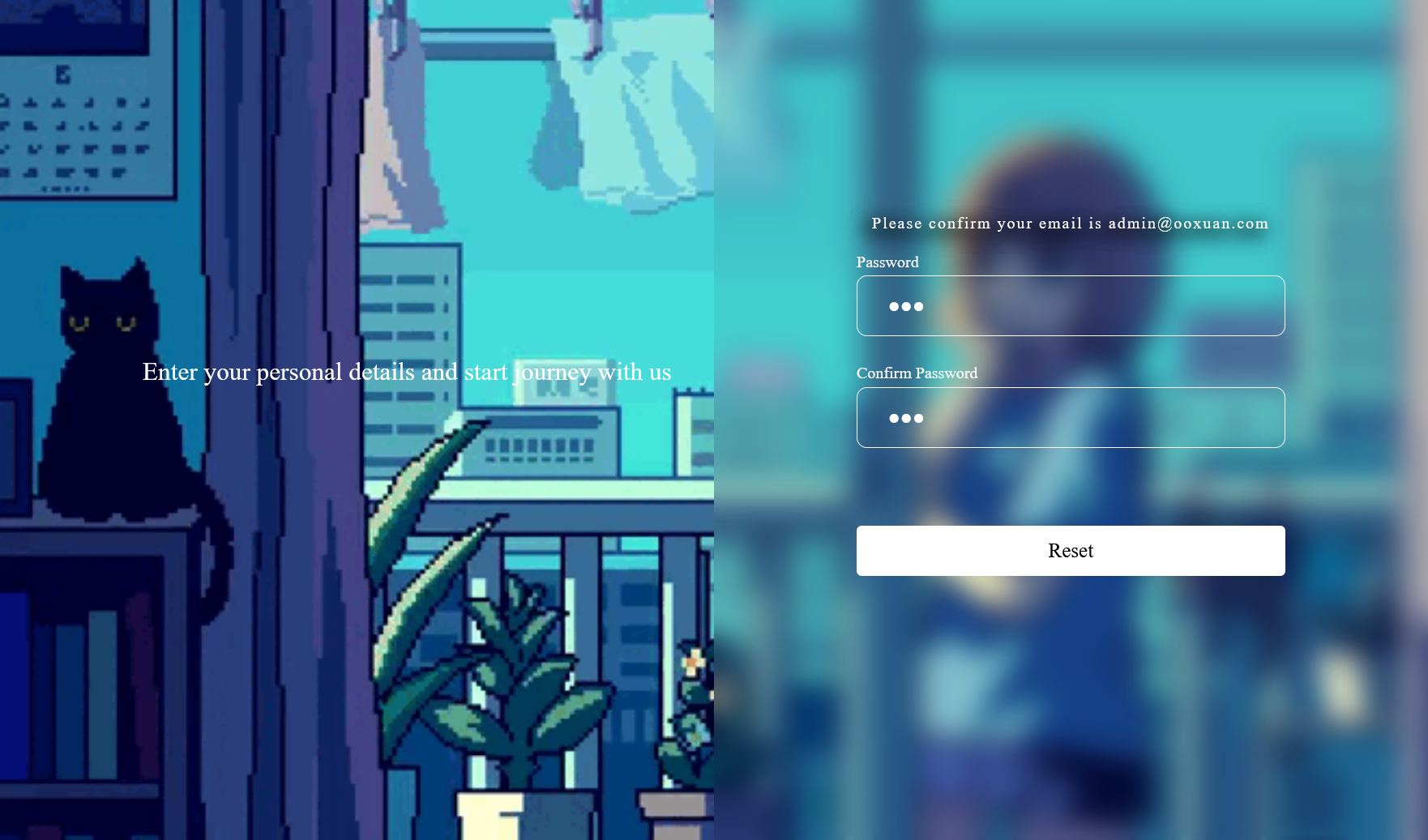
随便改个,然后返回登录
得到flag

flag{ab071433-0664-485c-94dc-a6aa983c56d0}
重生之我不是大宝
题目

先F12看源码,发现有请求的就一个地方,但是一直没有触发
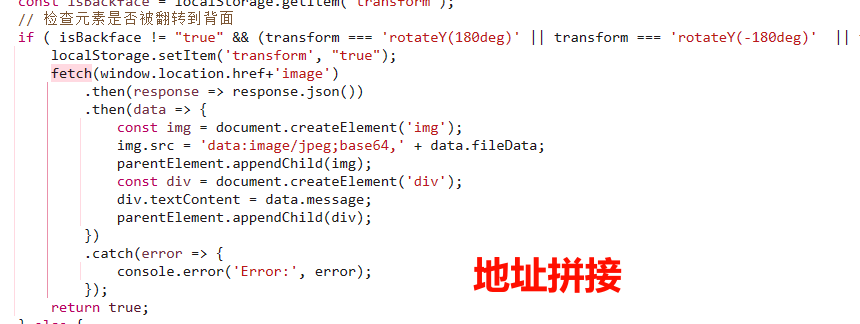
直接我们手动接上访问
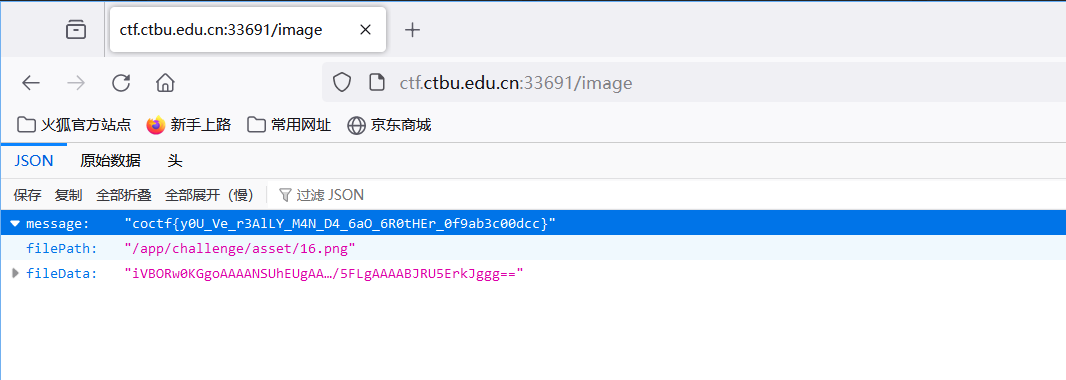
出了
coctf{y0U_Ve_r3AlLY_M4N_D4_6aO_6R0tHEr_0f9ab3c00dcc}
Reverse
random
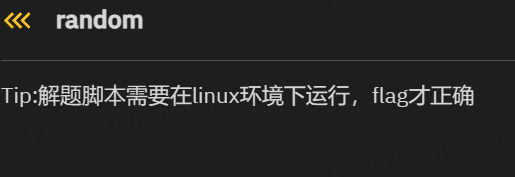
先ida打开
进入flag函数
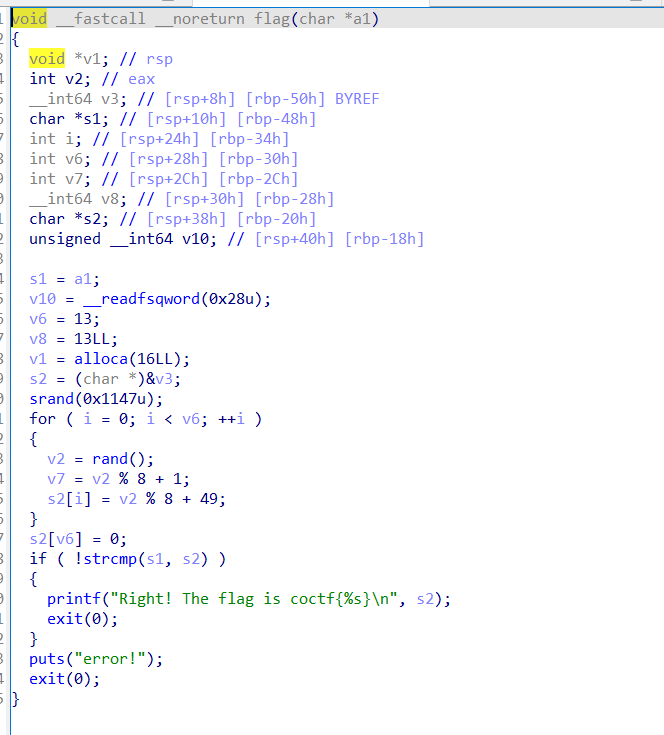
void __fastcall __noreturn flag(char *a1)
{
void *v1; // rsp
int v2; // eax
__int64 v3; // [rsp+8h] [rbp-50h] BYREF
char *s1; // [rsp+10h] [rbp-48h]
int i; // [rsp+24h] [rbp-34h]
int v6; // [rsp+28h] [rbp-30h]
int v7; // [rsp+2Ch] [rbp-2Ch]
__int64 v8; // [rsp+30h] [rbp-28h]
char *s2; // [rsp+38h] [rbp-20h]
unsigned __int64 v10; // [rsp+40h] [rbp-18h]
s1 = a1;
v10 = __readfsqword(0x28u);
v6 = 13;
v8 = 13LL;
v1 = alloca(16LL);
s2 = (char *)&v3;
srand(0x1147u);
for ( i = 0; i < v6; ++i )
{
v2 = rand();
v7 = v2 % 8 + 1;
s2[i] = v2 % 8 + 49;
}
s2[v6] = 0;
if ( !strcmp(s1, s2) )
{
printf("Right! The flag is coctf{%s}\n", s2);
exit(0);
}
puts("error!");
exit(0);
}生成的随机字符串是根据 rand() 函数生成的,它的种子固定
因为题目说了要在Linux下,所以就用在线页面
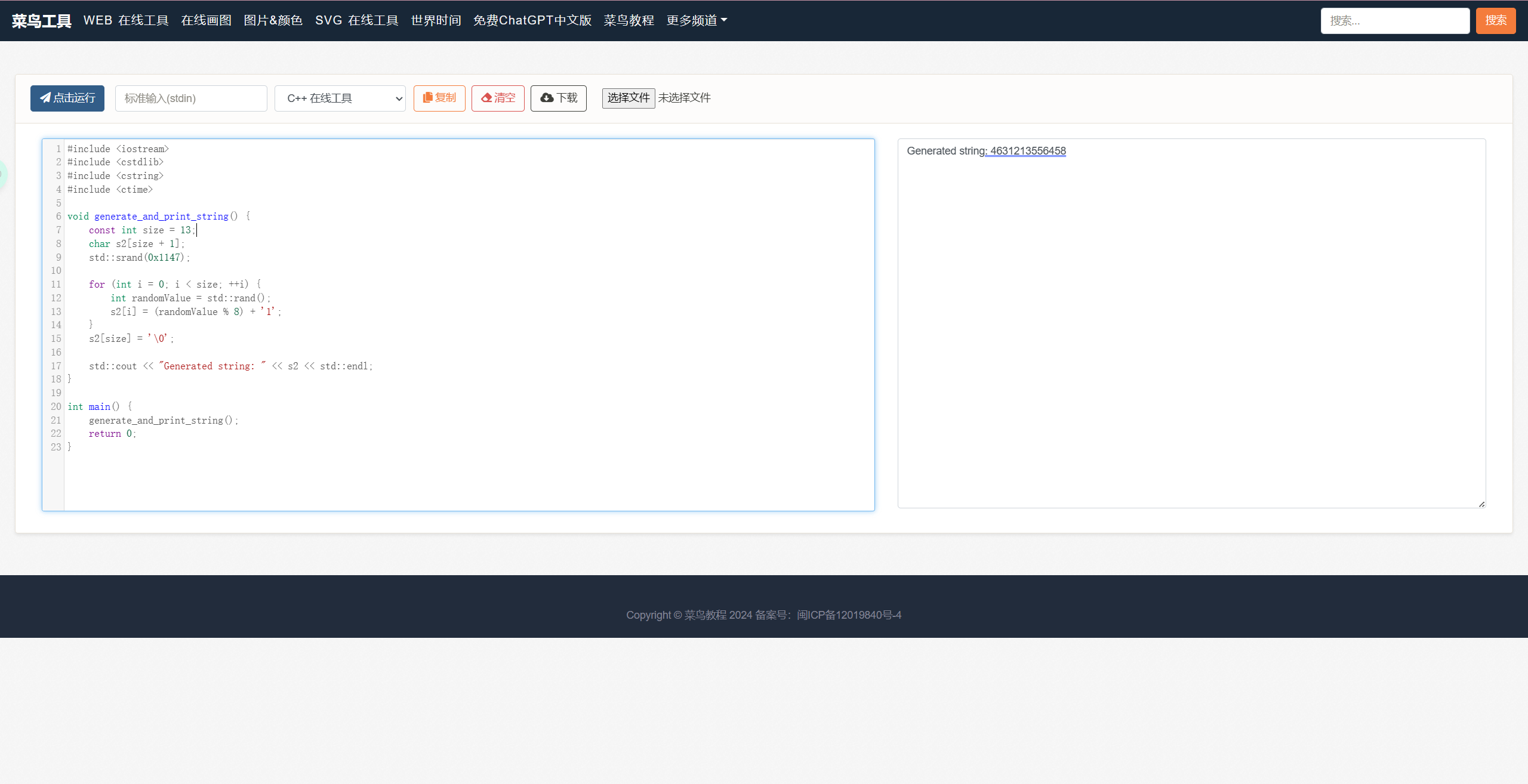
得到4631213556458
然后直接套个壳就是了
coctf{4631213556458}
easy_z3
题目为
def flag_checker(v, w, x, y, z):
if (v * 23 + w * -32 + x * 98 + y * 55 + z * 90 == 123081) and \
(v * 123 + w * -322 + x * 68 + y * 67 + z * 32 == -421103) and \
(v * 266 + w * -34 + x * 43 + y * 8 + z * 32 == 560626) and \
(v * 343 + w * -352 + x * 58 + y * 65 + z * 5 == -3364) and \
(v * 231 + w * -321 + x * 938 + y * 555 + z * 970 == 1236226):
print("Congratulations, Here is your flag:")
print(f"coctf{{{v}_{w}_{x}_{y}_{z}}}")
else:
print("\nSeems your luck is not in favor right now!\nBetter luck next time!")
v, w, x, y, z = map(int, input("Input 5 random numbers (separated by spaces): ").split())
print()
flag_checker(v, w, x, y, z)扔解方程的网站就好了
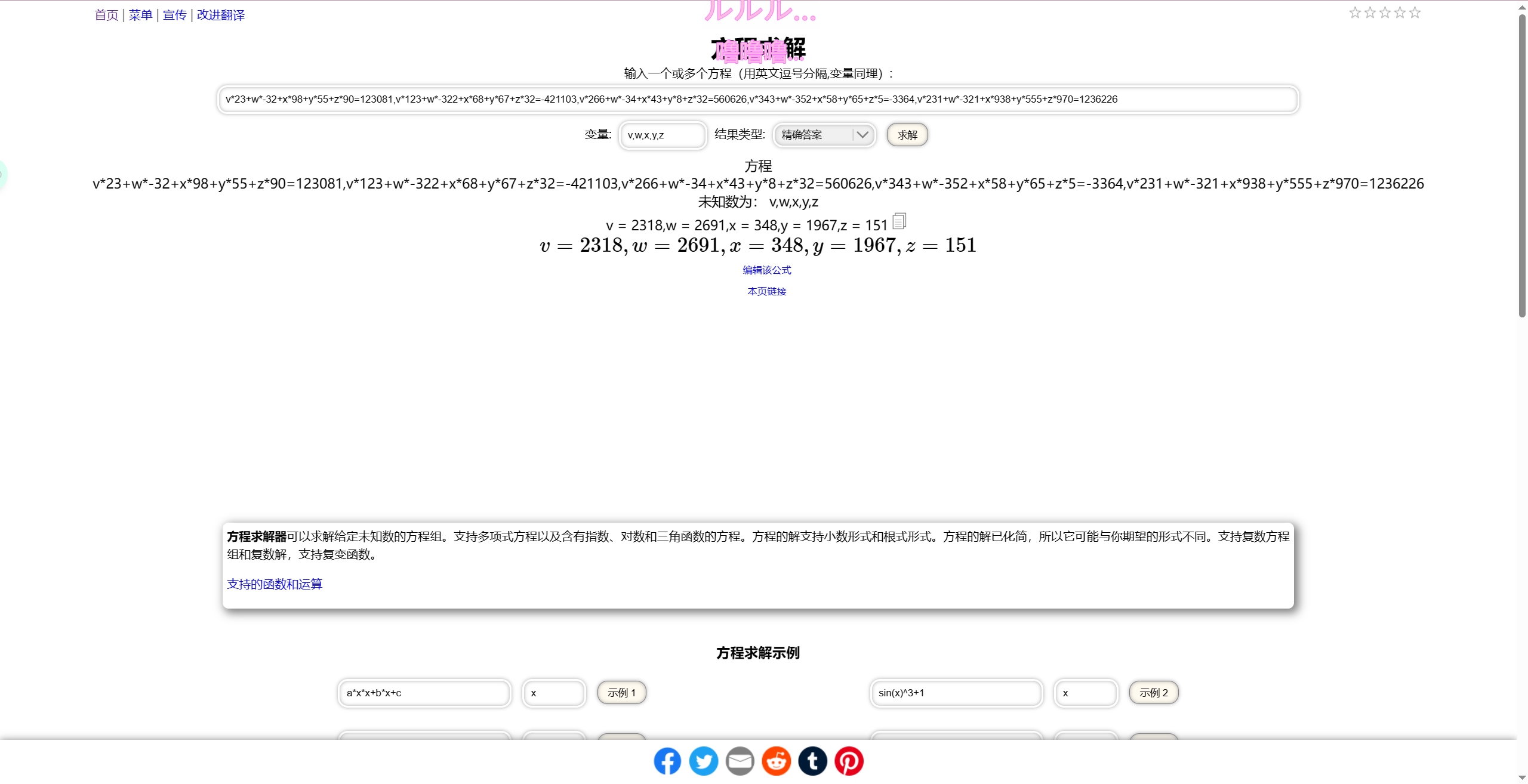
得到 v = 2318 w = 2691 x = 348 y = 1967 z = 151
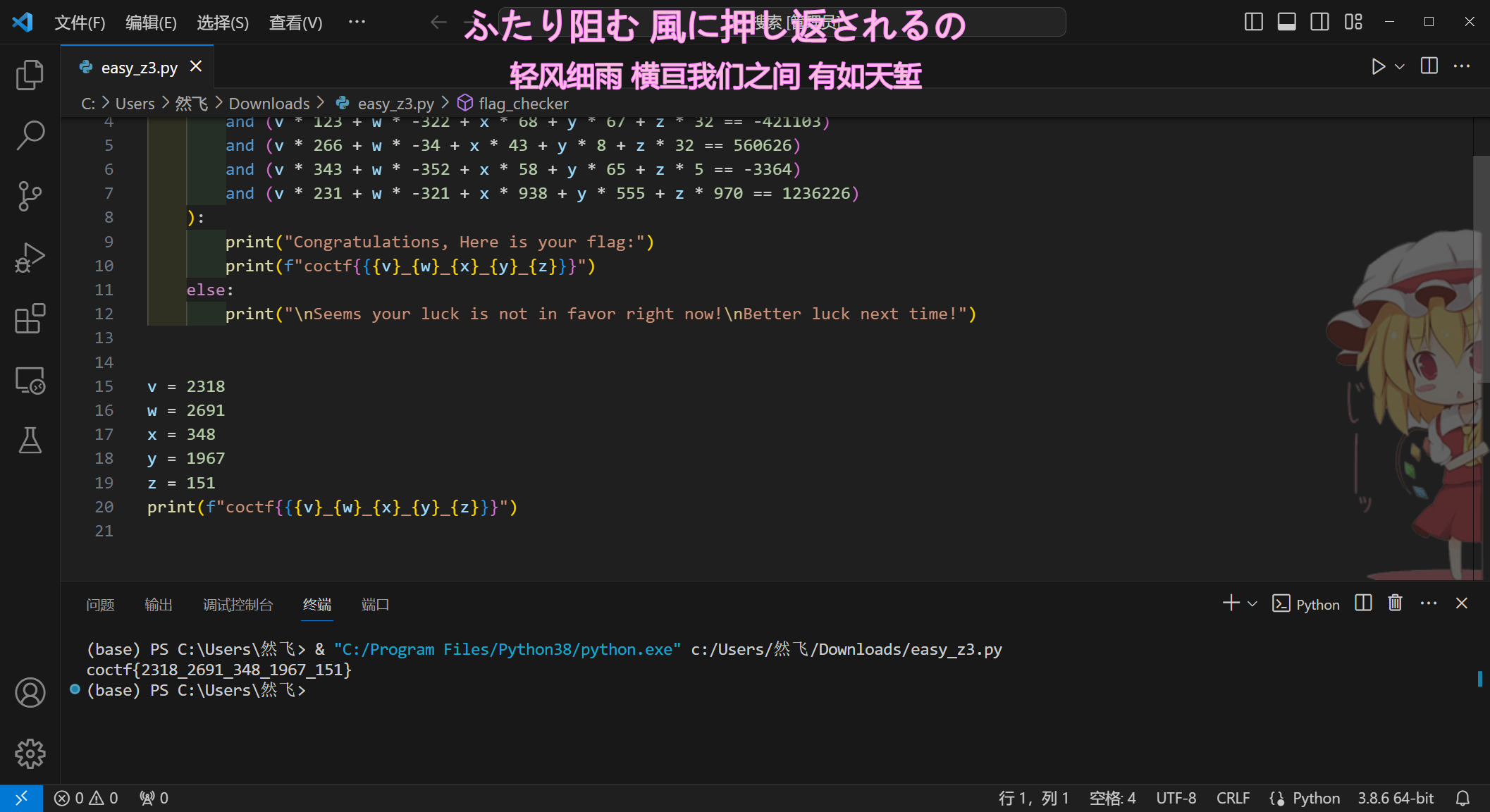
coctf{2318_2691_348_1967_151}
sign_in
签到题
ida打开
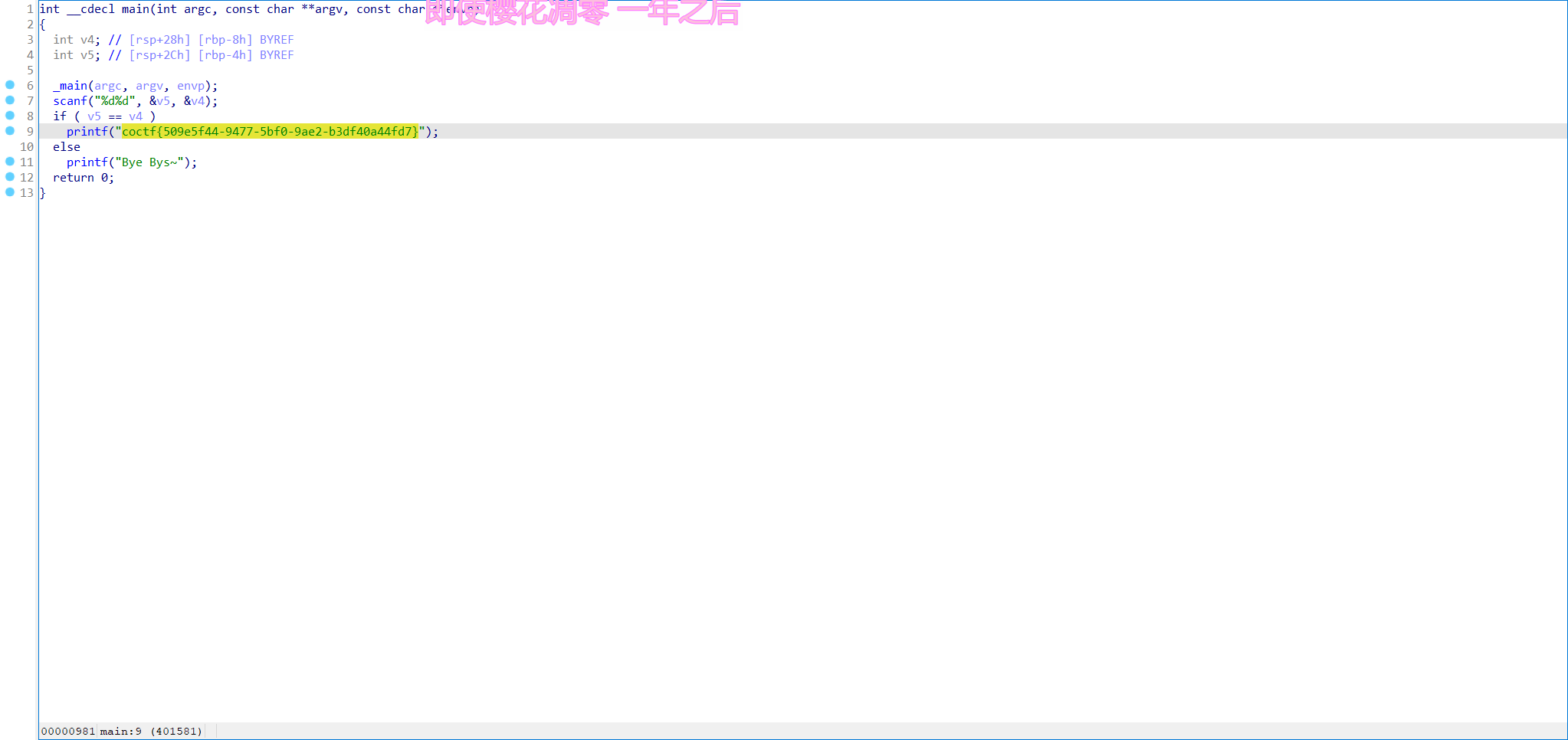
coctf{509e5f44-9477-5bf0-9ae2-b3df40a44fd7}
简单的逻辑
题目为
.text:0804850B public crypto
.text:0804850B crypto proc near ; CODE XREF: main+73↓p
.text:0804850B
.text:0804850B var_8 = dword ptr -8
.text:0804850B var_4 = dword ptr -4
.text:0804850B arg_0 = dword ptr 8
.text:0804850B arg_4 = dword ptr 0Ch
.text:0804850B
.text:0804850B ; __unwind {
.text:0804850B push ebp
.text:0804850C mov ebp, esp
.text:0804850E sub esp, 10h
.text:08048511 mov [ebp+var_8], 0
.text:08048518 jmp short loc_804854B
.text:0804851A ; ---------------------------------------------------------------------------
.text:0804851A
.text:0804851A loc_804851A: ; CODE XREF: crypto+46↓j
.text:0804851A mov [ebp+var_4], 40h ; '@'
.text:08048521 jmp short loc_8048541
.text:08048523 ; ---------------------------------------------------------------------------
.text:08048523
.text:08048523 loc_8048523: ; CODE XREF: crypto+3A↓j
.text:08048523 mov edx, [ebp+var_8]
.text:08048526 mov eax, [ebp+arg_0]
.text:08048529 add eax, edx
.text:0804852B mov ecx, [ebp+var_8]
.text:0804852E mov edx, [ebp+arg_0]
.text:08048531 add edx, ecx
.text:08048533 movzx ecx, byte ptr [edx]
.text:08048536 mov edx, [ebp+var_4]
.text:08048539 xor edx, ecx
.text:0804853B mov [eax], dl
.text:0804853D add [ebp+var_4], 1
.text:08048541
.text:08048541 loc_8048541: ; CODE XREF: crypto+16↑j
.text:08048541 cmp [ebp+var_4], 42h ; 'B'
.text:08048545 jle short loc_8048523
.text:08048547 add [ebp+var_8], 1
.text:0804854B
.text:0804854B loc_804854B: ; CODE XREF: crypto+D↑j
.text:0804854B mov eax, [ebp+var_8]
.text:0804854E cmp eax, [ebp+arg_4]
.text:08048551 jl short loc_804851A
.text:08048553 nop
.text:08048554 leave
.text:08048555 retn
.text:08048555 ; } // starts at 804850B
.text:08048555 crypto endp
int main() {
FILE* file;
int length = 43;
char text[44];
file = fopen("flag.txt", "r");
fread(text, 1, length, file);
text[length] = '.text:0804850B public crypto
.text:0804850B crypto proc near ; CODE XREF: main+73↓p
.text:0804850B
.text:0804850B var_8 = dword ptr -8
.text:0804850B var_4 = dword ptr -4
.text:0804850B arg_0 = dword ptr 8
.text:0804850B arg_4 = dword ptr 0Ch
.text:0804850B
.text:0804850B ; __unwind {
.text:0804850B push ebp
.text:0804850C mov ebp, esp
.text:0804850E sub esp, 10h
.text:08048511 mov [ebp+var_8], 0
.text:08048518 jmp short loc_804854B
.text:0804851A ; ---------------------------------------------------------------------------
.text:0804851A
.text:0804851A loc_804851A: ; CODE XREF: crypto+46↓j
.text:0804851A mov [ebp+var_4], 40h ; '@'
.text:08048521 jmp short loc_8048541
.text:08048523 ; ---------------------------------------------------------------------------
.text:08048523
.text:08048523 loc_8048523: ; CODE XREF: crypto+3A↓j
.text:08048523 mov edx, [ebp+var_8]
.text:08048526 mov eax, [ebp+arg_0]
.text:08048529 add eax, edx
.text:0804852B mov ecx, [ebp+var_8]
.text:0804852E mov edx, [ebp+arg_0]
.text:08048531 add edx, ecx
.text:08048533 movzx ecx, byte ptr [edx]
.text:08048536 mov edx, [ebp+var_4]
.text:08048539 xor edx, ecx
.text:0804853B mov [eax], dl
.text:0804853D add [ebp+var_4], 1
.text:08048541
.text:08048541 loc_8048541: ; CODE XREF: crypto+16↑j
.text:08048541 cmp [ebp+var_4], 42h ; 'B'
.text:08048545 jle short loc_8048523
.text:08048547 add [ebp+var_8], 1
.text:0804854B
.text:0804854B loc_804854B: ; CODE XREF: crypto+D↑j
.text:0804854B mov eax, [ebp+var_8]
.text:0804854E cmp eax, [ebp+arg_4]
.text:08048551 jl short loc_804851A
.text:08048553 nop
.text:08048554 leave
.text:08048555 retn
.text:08048555 ; } // starts at 804850B
.text:08048555 crypto endp
int main() {
FILE* file;
int length = 43;
char text[44];
file = fopen("flag.txt", "r");
fread(text, 1, length, file);
text[length] = '\0';
fclose(file);
crypto(text, length);
printf("%s\n", text);
return 0;
}
, 7%8zwq{uz &n"'"!nr%!snr%rsn&{u'rsp{v'zw>
';
fclose(file);
crypto(text, length);
printf("%s\n", text);
return 0;
}
, 7%8zwq{uz &n"'"!nr%!snr%rsn&{u'rsp{v'zw>
把上面的汇编转化为C语言,然后在小改一下
因为这个是用了异或,加密也是解密,直接运行就好了
#include <stdio.h>
void crypto(char* data, int length) {
char var_8 = 0;
char var_4 = 0x40;
for (var_8 = 0; var_8 < length; var_8++) {
for (var_4 = 0x40; var_4 <= 0x42; var_4++) {
data[var_8] ^= var_4;
}
}
}
int main() {
FILE* file;
int length = 43;
char text[44]="7%8zwq{uz &n\"'\"!nr%!snr%rsn&{u'rsp{v'zw>";
crypto(text, length);
printf("%s\n", text);
return 0;
}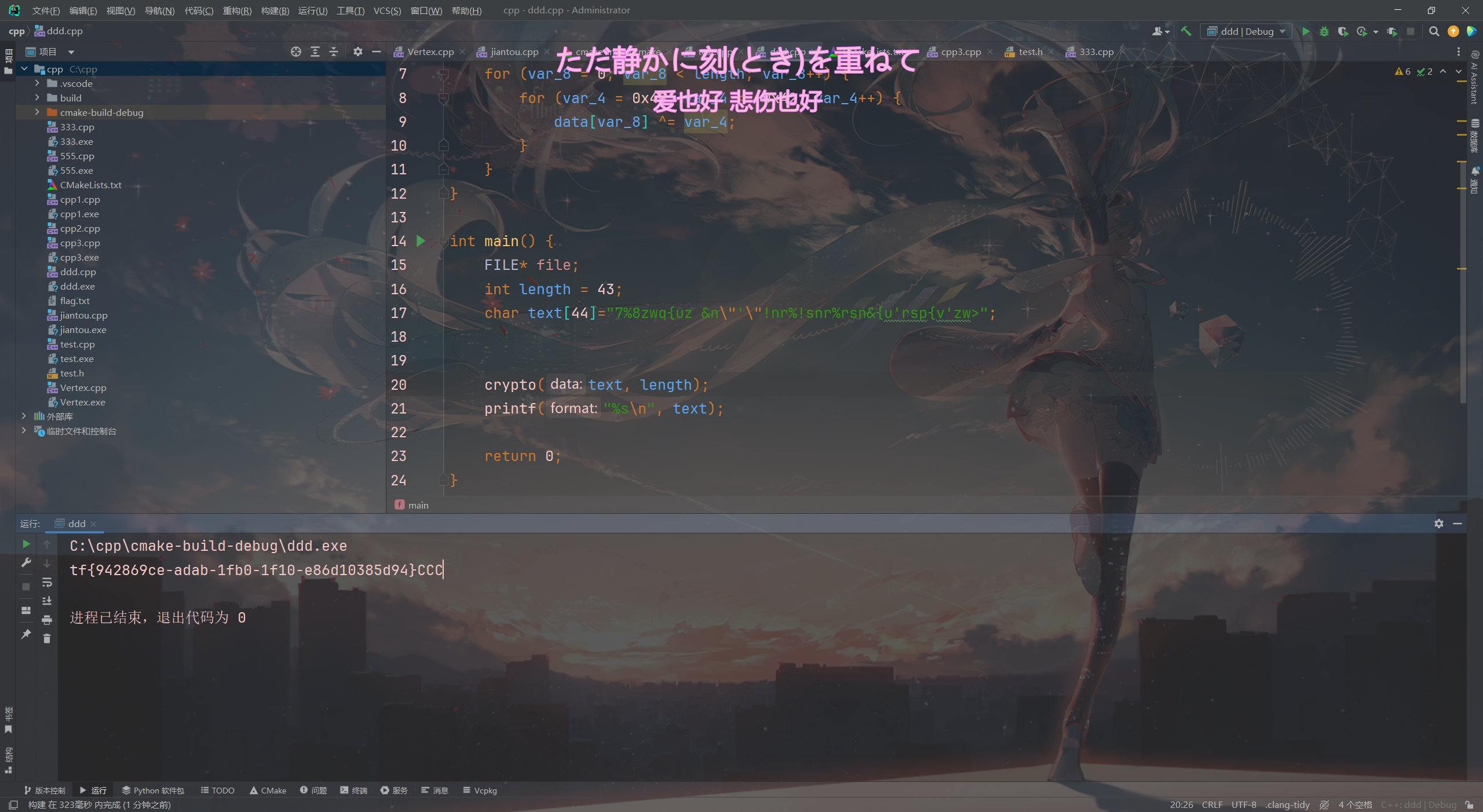
有点小错误是\"造成的不过不影响
coctf{942869ce-adab-1fb0-1f10-e86d10385d94}








Comments NOTHING