星のflag: 瓦豆鲁德篇
拿到小程序源码
https://docs.pingcode.com/baike/3361095
抓包拿到源码文件
可以直接下载下来
zstd是个压缩格式,而bandzip支持解压
解压出来后为一个二进制文件,但是用010可以看到里面其实就是源码,直接txt打开复制出里面的源码
直接搜索flag头可以定位到生成位置
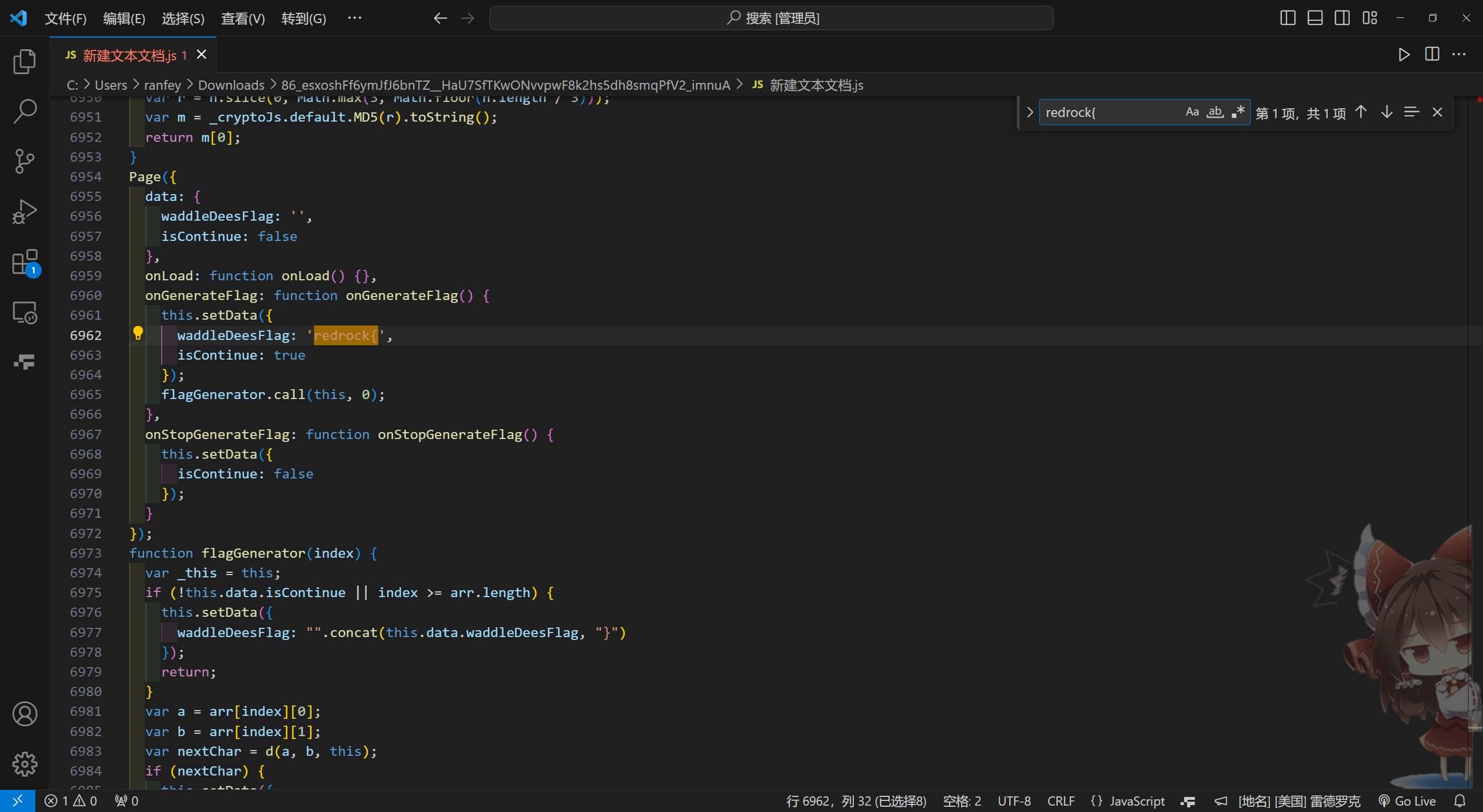
可以看到,是一步步拼接到waddleDeesFlag上面的,每个字符由d函数生成,且传入的a,b为arr
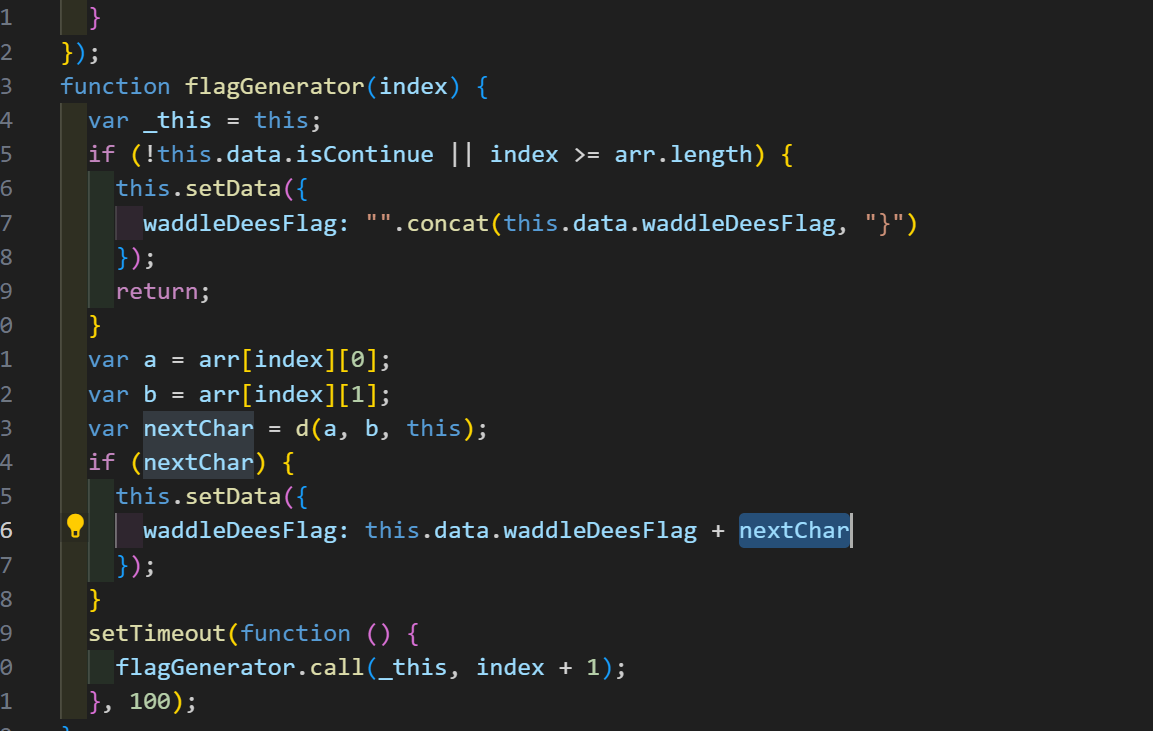
定位到d函数,arr也在上面
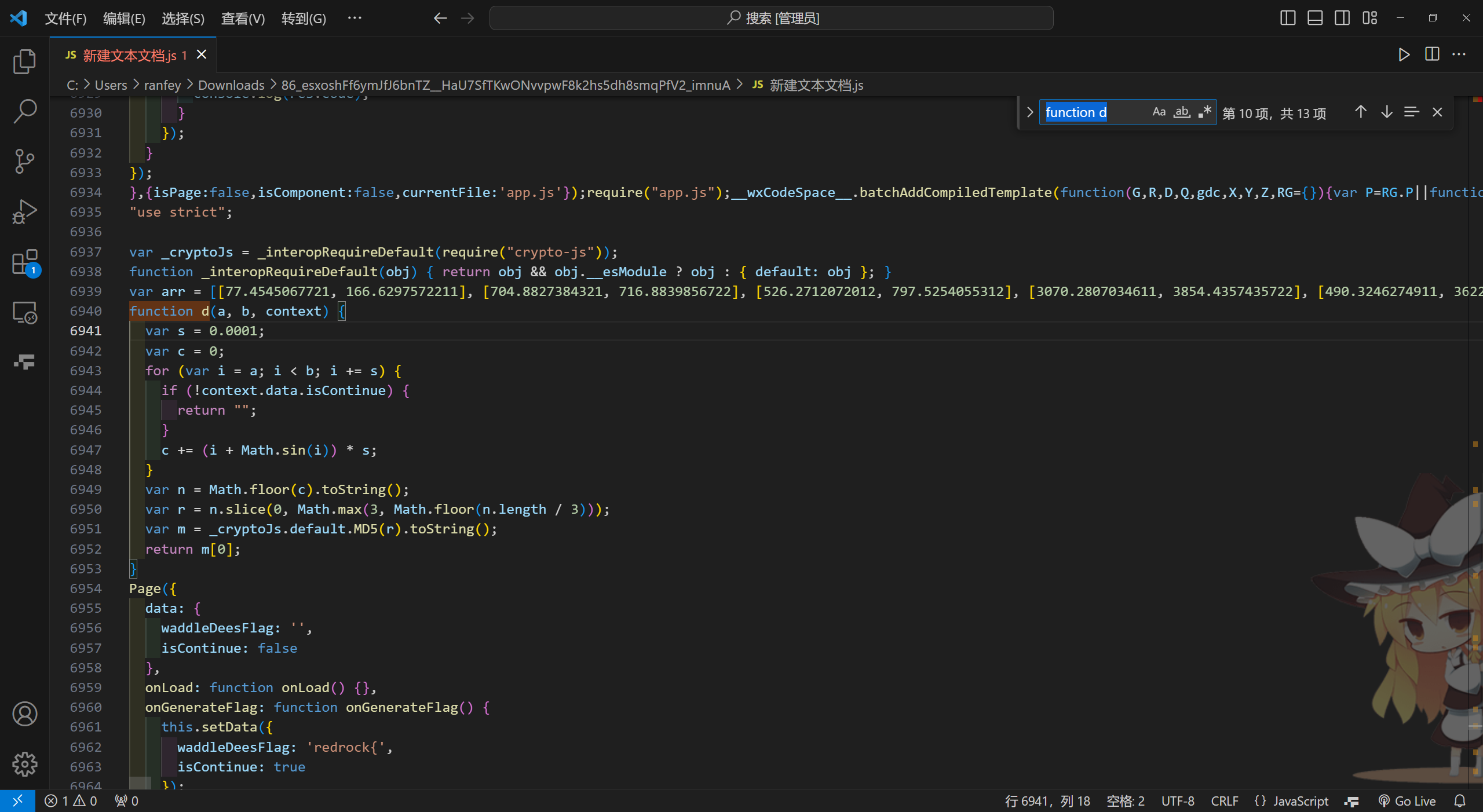
var arr = [[77.4545067721, 166.6297572211], [704.8827384321, 716.8839856722], [526.2712072012, 797.5254055312], [3070.2807034611, 3854.4357435722], [490.3246274911, 36224.8858838722], [41404.3166443722, 41673.1503183722], [6787.6554038721, 46854.1678526621], [69504.4221148712, 418677.4399131722], [587395.8927547721, 646218.371960242], [23378.1410475611, 862165.0667217221], [3425775.220405308, 3679455.7534740176], [21376195.152235862, 57806775.24392879], [136548100.36301744, 2126740322.7827096], [3025384212.2862115, 42887118354.86438], [2749728.820111889, 20752727.611226656], [38414630.64337055, 313629634.4837362], [33882710.842073366, 345902224.4626296], [63832518.65776362, 224151175.8626729], [713381630.9568518, 2361680166.434476], [943572305.6985991, 3249761735.8722763], [2182238279.357637, 4762311856.787363], [2449920231.2722983, 6453724258.242947], [5251427633.228511, 42202975021.22658], [3586474625.7261167, 36828433774.11296], [2438575572.788131, 36686266931.434525], [87043816613.20274, 297732697735.6053], [472044465269.30133, 528171386733.36865], [312425872025.35376, 807318802980.8772], [353533120613.98065, 825428116861.4183], [504334778467.7691, 1610323225786.69955], [573352925673.3484, 8466494214312.498], [6291764415342.347, 10584266511691.768], [38252576539970.57, 56553309176751.18], [36782537271527.62, 57371110527665.5]];
function d(a, b, context) {
var s = 0.0001;
var c = 0;
for (var i = a; i < b; i += s) {
if (!context.data.isContinue) {
return "";
}
c += (i + Math.sin(i)) * s;
}
var n = Math.floor(c).toString();
var r = n.slice(0, Math.max(3, Math.floor(n.length / 3)));
var m = _cryptoJs.default.MD5(r).toString();
return m[0];
}每一次c都是通过 for 循环从 a 迭代到 b,每次累加 MARKDOWN_HASH03c7c0ace395d80182db07ae2c30f034MARKDOWNHASH,是一个微分
$$
c=\int{a}^{b}(i+sin(i))di= \left [ \frac{i^2}{2} -cos(i) \right ]_{a}^{b}=(\frac{b^2}{2} -cos(b))-(\frac{a^2}{2} -cos(a))
$$
把微分方程转为积分,然后解出来就可以把循环去掉,变为一个简单的减法
小程序直接跑可以跑到redrock{aa8726a2c7c开头,可以用来校验
可以得到
import numpy as np
import hashlib
arr = [
[77.4545067721, 166.6297572211],
[704.8827384321, 716.8839856722],
[526.2712072012, 797.5254055312],
[3070.2807034611, 3854.4357435722],
[490.3246274911, 36224.8858838722],
[41404.3166443722, 41673.1503183722],
[6787.6554038721, 46854.1678526621],
[69504.4221148712, 418677.4399131722],
[587395.8927547721, 646218.371960242],
[23378.1410475611, 862165.0667217221],
[3425775.220405308, 3679455.7534740176],
[21376195.152235862, 57806775.24392879],
[136548100.36301744, 2126740322.7827096],
[3025384212.2862115, 42887118354.86438],
[2749728.820111889, 20752727.611226656],
[38414630.64337055, 313629634.4837362],
[33882710.842073366, 345902224.4626296],
[63832518.65776362, 224151175.8626729],
[713381630.9568518, 2361680166.434476],
[943572305.6985991, 3249761735.8722763],
[2182238279.357637, 4762311856.787363],
[2449920231.2722983, 6453724258.242947],
[5251427633.228511, 42202975021.22658],
[3586474625.7261167, 36828433774.11296],
[2438575572.788131, 36686266931.434525],
[87043816613.20274, 297732697735.6053],
[472044465269.30133, 528171386733.36865],
[312425872025.35376, 807318802980.8772],
[353533120613.98065, 825428116861.4183],
[504334778467.7691, 1610323225786.69955],
[573352925673.3484, 8466494214312.498],
[6291764415342.347, 10584266511691.768],
[38252576539970.57, 56553309176751.18],
[36782537271527.62, 57371110527665.5],
]
def d(a, b):
integral = lambda x: (x**2) / 2 - np.cos(x)
c = integral(b) - integral(a)
n = str(int(c))
r = n[: max(3, len(n) // 3)]
m = hashlib.md5(r.encode()).hexdigest()
return m[0]
flag = "redrock{"
for a, b in arr:
flag += d(a, b)
flag += "}"
print(flag)redrock{aa8726a2c7c371195027ddce083df71983}








Comments NOTHING